 INFORMATION SECURITY SKILLS ACCREDITATION IN AUSTRALIA
INFORMATION SECURITY SKILLS ACCREDITATION IN AUSTRALIA
Sport and the Arts
The Current State and
Industry Consensus
on the Way Forward
Communications,
Act 1982 by the Department of Infrastructure,
Development,
under the FOI
Released Transport, Regional
FINAL VERSION FOR CIRCULATION
SIFT Pty Ltd
Date: November 2005
Table of Contents
1 EXECUTIVE SUMMARY
3
2 PROJECT BACKGROUND & CONTEXT
8
2.1
DEFINITIONS
8
2.2
BACKGROUND
8
Arts
2.3
LOCAL CONTEXT
9
2.4
INTERNATIONAL CONTEXT 10
the
3. THE CURRENT STATE 13
3.1
AVAILABLE QUALIFICATIONS 13
and
3.2
KNOWLEDGE 18
3.3
TRUSTWORTHINESS 24
3.4
E
Infrastructure,
XPERIENCE 25
4 THE NEED 28
of Sport
4.1
THE NEED FOR A MECHANISM TO ACCURATELY ASSESS COMPETENCE 29
4.2
THE NEED FOR INFORMATION SECURITY PROFESSIONALS TO POSSESS GREATER
KNOWLEDGE 30
4.3 THE NEED FOR PROFESSIONALS TO POSSESS KNOWLEDGE AND UNDERSTANDING
SPECIFIC TO THE AUSTRALIAN BUSINESS MARKET 32
4.4
THE NEED FOR AN INFORMED MARKET 35
5 THE WAY FORWARD 37
Department
5.1
CONTEXT OF OPTIONS 37
5.2
GENERALLY ACCEPTED PRINCIPLES 38
the
5.3
CONTENT 39
5.4
PROPOSED APPROACHES 43
by Communications,
5.5
DEMAND AND SUPPLY DRIVERS 49
6 CONSENSUS 50
6.1
CONSENSUS TOWARD AN INDUSTRY AWARENESS PROGRAM 50
1982
6.2
CONSENSUS TOWARDS A TRAINING COMPONENT 53
7 APPENDIX A: PARTICIPANTS 57
Act
8 APPENDIX B - SUMMARY OF PARTICIPATING ORGANISATIONS 63
9 APPENDIX C: 17799 MAPPING FOR CISSP, CISA, CISM AND ISSPCS
Development,
(PRACTITIONER LEVEL)
FOI
72
10 APPENDIX D: BIBLIOGRAPHY 93
the
Table of figures
Figure 1: Elements of a successful accreditation program 37
Figure 2: Proposed approaches and levels of industry support 43
Regional
Figure 3: Spectrum of industries and sector areas 64
under
Released Transport,
IT Security Skills Accreditation in Australia
1
Executive Summary
The purpose of this project was to examine the current information technology (IT) security
qualifications available to Australian IT security professionals, to produce a ‘state-of-play’
report and to examine the need for, role and possible structure & governance arrangements of
an IT security accreditation/certification scheme. This report includes a comprehensive
review of the current industry and the views of individuals and organisations in industry and
Arts
government regarding the need for an additional security skills accreditation or certification
scheme.
the
SIFT Pty Ltd was awarded the consultancy to undertake the project.
Representatives from more than 40 stakeholder organisations contributed to this report
and
through interviews, round table discussions and commentary during the course of the project
and at an industry workshop sponsored by Department of Communications, Information
Infrastructure,
Technology & the Arts (DCITA) held for this purpose. Contributors included:
of Sport
Accreditation and certification bodies;
Industry associations for the information technology (IT), IT security, and
information security industries
1;
Consumers of information security professional services, including representatives
from the banking and finance, telecommunications, Government, and utilities
sectors;
Department
Bodies representing the interests of small to medium enterprises (SMEs);
Representatives of universities and TAFE; and
the
Organisations involved in the recruitment and placement of information security
Communications,
professionals.
by
The Australian information security community has more than 50 certification schemes
available. These include industry recognised international schemes, vendor and product-
1982
specific certifications, Government-endorsed certification schemes and academic degrees
and diplomas. The majority of information security qualifications currently available in
Australia are owned, administered and regulated by overseas organisations.
Act
Based on wide-ranging discussions with key stakeholders four main ‘needs’ were identified in
the Australian information security skills marketplace. These needs are:
FOI Development,
the need for a mechanism to accurately assess competence;
the
the need for information security professionals to possess greater knowledge;
the need for professionals to possess knowledge and understanding specific to
the Australian business environment; and
under Regional
the need for an informed market.
Discussions surrounding these ‘needs’ lead to the identification of a series of related points:
To enable market forces for IT security skills to successfully operate, consumers
of information security services and employers of information security
professionals need to have access to information about skills available in the
Released Transport,
1 The term “IT security” is considered to be a subset of information security.
Page 3 of 98
IT Security Skills Accreditation in Australia
market, including knowledge about existing qualifications and certifications and
what these represent;
Due to the global nature of the industry it is important that the qualifications, skills,
knowledge and experience of Australian security professionals should continue to
be recognised on an international level notwithstanding the value placed on
specific Australian knowledge and experience by Australian
consumers/employers;
Arts
All practising security professionals should be able to access any new knowledge
development activities, regardless of previous certification
the
qualifications/certifications; and
The majority of stakeholders consider that existing programs are meeting the
and
industry’s need to be able to accurately assess the competence of individuals with
specific qualifications/certifications and there is no need to develop a new
Infrastructure,
information security skills accreditation scheme for Australia.
of Sport
A range of approaches were developed by the consultant and discussed with stakeholders.
During discussions, a number of key principles emerged as crucial for the acceptance and
success of any new approach to IT security skills accreditation. Any new approach should:
build on existing certification programs;
be open and recognise other international certifications already in existence as
well as academic qualifications;
Department
minimise any additional costs to ensure value for money and accessibility;
maintain vendor neutrality;
the
be supported by both providers and consumers; and
by Communications,
not be viewed by consumers/employers as a substitute for due diligence in
verifying the qualifications, skills and knowledge of potential
contractors/employees.
1982
Industry Workshop
A workshop was held in June 2005 in Sydney to inform stakeholders of the consultant’s
Act
stage 1 findings and to present five possible approaches for a way forward. All
individuals/organisations interviewed for the first stage of the report were invited to the
FOI Development,
workshop. The options put forward to workshop participants were:
•
Market forces: To continue to allow the direction of accreditation and certification in
the
Australia to be determined by industry market forces.
Workshop participants reacted positively towards the current certification
programs which have evolved due to market forces, and acknowledged the
under Regional
continuing work by certification bodies to meet the changing and developing
needs of industry.
•
Licensing and registration: Information security professionals could be required to
register with a licensing program in order to practise in the industry.
Workshop participants were opposed to the introduction of a mandatory licensing
Released Transport,
and registration scheme, and without industry support it was agreed that the
model should not be pursued further.
Page 4 of 98
IT Security Skills Accreditation in Australia
•
Program accreditation: An accreditation scheme for certification providers could be
established. Participants discussed existing mechanisms for accrediting certification
bodies, including ISO/IEC 17024-2004: Conformity Assessment – General requirements
for bodies operating certification of persons.
As participants noted that certification providers, rather than individual
professionals can already obtain accreditation to international standards, to
ensure the quality and integrity of certification programs this approach was not
Arts
pursued further.
the
•
Awareness program: An information program could be developed to assist
organisations and professionals understand the range, relevance and content of IT
security qualifications available in Australia.
and
Workshop participants indicated strong support for an awareness program to
Infrastructure,
provide information to both security professionals and consumers/employers of
security services, on certifications available to the Australian market. Participants
of Sport
discussed how such a program could encompass a
Buyers’ Guide describing the
range of qualifications held by IT security professionals in Australia. It was noted
that to be viable this program would need to be supported by both certification
providers, academic institutions and the consumer/employers of IT security
services.
•
Consumer protection: Standard form contracts for common IT security services could
Department
be developed to improve the quality and consistency of services provided by
professionals.
the
It was suggested by some participants that consumer law could afford some
protection for organisations, particularly for SMEs acquiring information security
by Communications,
services. There was however agreement that standard form contracts alone could
not ensure that professionals were able to meet individual organisation’s
requirements.
1982
It was noted that the utility of consumer protection mechanisms, such as standard
form contracts was minimal as large consumers/employers of information security
Act
professional services would generally already use internal legal and compliance
personnel and associated contracts.
FOI Development,
Participant’s Conclusions
•
Market forces will determine the need for new Australian certification programs
the
When presented with the consultant’s findings and potential models, the majority of
participants agreed that current certification programs are meeting industry requirements and
there is neither a compelling need, nor a compelling driver for the creation of a new Australian
under Regional
certification program.
•
Current certification programs can be used by buyers as a benchmark
Participants had differing views on the state of accreditation in Australia but generally
conceded that current certification programs are valuable as a benchmark as they
demonstrate a professional’s degree of understanding, dedication and discipline in the
Released Transport,
industry. It was agreed that any gaps between certification programs and industry standards
Page 5 of 98
IT Security Skills Accreditation in Australia
were a reflection of the different targets set by each program and the rapidly changing needs
of consumers and employers.
•
Some gaps do exist between the supply of professionals & the demand for services
Participants agreed that there was scope for further discussion on whether existing
certifications could be enhanced in light of gaps identified by the project.
2
An Australian training component
Arts
An Australian training component was proposed as a solution to address the lack of regional
knowledge faced by professionals who practise in the Australian information security
the
environment. The Australian IT Security Training Component would include relevant domestic
issues and inform information security professionals on Australian legislation and regulation
and
requirements, such as the Privacy Act and Australian telecommunications legislation.
Such a component would be offered as an additional option within existing certification and
Infrastructure,
qualification schemes available in Australia.
of Sport
It was emphasised by participants that the purpose of the Australian training component
would be to create a reference level of knowledge and not to train information security
professionals to become ‘legal experts’. It was accepted that professionals should have an
understanding and awareness of Australia’s legal and regulatory environment in order to
practise information security within legal boundaries.
Awareness of Certification Programs
Department
Participants agreed that consumers/employers of information security services needed to be
better informed as to what existing certifications represent. It was observed that many
the
consumers/employers of IT Security services do not understand the relative positioning of
by Communications,
existing programs, nor are they able to identify the different skill sets of professionals holding
different certifications.
There was broad stakeholder agreement that consumers/employers also need general
1982
assistance to be able to accurately assess the competence of specific individuals.
To achieve this objective a number of organisations proposed the concept of a Buyer’s Guide
Act
as the medium for information on programs. However, it was acknowledged that a Buyer’s
Guide could not be expected in one stroke to solve all information issues in the industry. It
was agreed that all the following items would provide valuable information to both
FOI Development,
consumers/employers of information security services and information security professionals
themselves.
the
1. An explanation of the differences between IT security and information security.
2. Descriptions of common roles and responsibilities for job roles within the
information security industry.
under Regional
3. A list of qualifications including information security programs offered by
certification bodies, various educational institutions and universities. Content
should be easily comprehensible and should summarise the skills and knowledge
2 As the objective of this project was to determine both stakeholder acceptance and possible governance arrangements for an IT security skills
accreditation/certification scheme, options for possible governance structures were canvassed with representatives interviewed. The industry consensus was
Released Transport,
that no new scheme should be developed; these structures are discussed briefly in the full report, but not in the Executive Summary.
Page 6 of 98
IT Security Skills Accreditation in Australia
examined as well as the requirement for continuing professional education by each
qualification.
4. A guide as to the technical abilities and management skills covered by each
qualification. It should also suggest which certifications could match specific job
roles.
5. An explanation of the ISO/IEC 17024 international accreditation standard and its
role in providing a quality assurance benchmark for certification bodies.
Arts
6. A directory of contacts for each qualification provider and relevant industry
associations.
the
It was agreed that a Buyers’ Guide could:
and
Provide an accepted point of reference with which to compare and contrast
certification schemes currently available;
Infrastructure,
Increase the confidence level of consumers in knowing when help is required for
of
information security;
Sport
Provide information on how to select the appropriate information security
professional for the job;
Inform consumers and professionals and allow them to select the most
appropriate program for their needs; and
Include pointers to relevant standards and methodologies.
Department
The Way Forward
In summary, participants representing a wide range of interests, were keen to continue to
the
encourage certification providers to respond to market forces, while supporting the
by Communications,
development of two initiatives, being:
An IT Security Accreditation Awareness Program (including an IT Security
Buyer’s Guide); and
1982
An Australian IT Security Training Component.
The Department of Communications, Information Technology & the Arts proposes that:
Act
this report be widely circulated to all participants;
Development,
the Department convene a group of interested industry and government agencies
FOI
to determine:
the
o
if there is broad agreement in the project’s conclusions; and
o if there is sufficient interest in the concept of an IT security
awareness program including a Buyers’ Guide to be developed
and funded by industry; and
under Regional
o if there is market support for an Australian IT security component.
November
2005
Released Transport,
Page 7 of 98
IT Security Skills Accreditation in Australia
2 PROJECT BACKGROUND & CONTEXT
2.1 DEFINITIONS
Arts
IT security is considered to be a subset of information security, although for the purpose of
this project, the terms were considered to be interchangeable on the basis that the two
professions have similar skill accreditation concerns.
the
The term “IT security skills” refers to the necessary competencies a professional would
require to appropriately and successfully secure an organisation’s IT systems.
and
“Information security skills” incorporates a slightly broader definition, referring to the
Infrastructure,
necessary competencies a professional would require to appropriately and successfully
secure an organisation’s information, whether within an IT system or elsewhere.
of Sport
It is acknowledged that the level and type of skills required in these fields will differ markedly
between job roles and organisation types.
2.2 BACKGROUND
The demand for information security professionals has continued to grow both in the public
Department
and private sectors over recent years. Information Security Interest Group (ISIG) Secretary
Mark Ames has estimated that there are between 1000 and 2000 information security
the
professionals currently working in Australia [LeMay 2005b].
by Communications,
In addition, there are a wide range of ICT professionals with considerable exposure to the
security field. The current marketplace offers a range of qualifications, from vendor and
product-specific certifications and internationally administered broad-based qualifications, to
1982
academic degrees and diplomas.
There has been ongoing discussion within industry associations on the need to develop a
Act
qualification tailored to the Australian marketplace. It was believed that such a scheme would
establish a common acceptable denominator – but not a lowest common denominator – for
information security practitioners and would allow for greater consumer choice and service
FOI Development,
[Ames, Gaskell & Muir 2003].
the
The issue of information security skills accreditation has received recognition at an
international level, including through the Asia-Pacific Economic Co-operation (APEC) and
International Federation for Information Processing (IFIP) forums.
Regional
IFIP Technical Committee 11 (Privacy and Security in Information Processing Systems)
under
released the following statement on Information Security Professionals at the 2002 annual
meeting in Cairo, Egypt:
TC-11 requests all member societies of IFIP to urge their relevant government
and education bodies to ensure that proper education and certification
requirements are set for those people who intend to become information security
Released Transport,
professionals and including those who audit the security of IT systems.
Page 8 of 98
IT Security Skills Accreditation in Australia
In particular, TC-11 recommends that:
Minimum education and training requirements be set for any such professionals;
Any such minimum educational and training requirements should reflect similar
standards in life professionals; and
Such education and training professionals be developed in line with emerging
international standards in the area of information security. [IFIP 2002]
Arts
The aim of this project was to evaluate the need for an Australian information security skills
accreditation scheme, and subsequently to summarise industry views on the way forward
the
[DCITA 2005]. The report combines findings derived from published literature, outcomes from
discussion held with key stakeholders and the examination of potential models for supporting
and
this area.
Infrastructure,
of
2.3 L
Sport
OCAL CONTEXT
A number of advocates have suggested that there is a need for an Australian qualification to
cater for local security issues, legislation and corporate governance requirements [LeMay
2005a]. Professor Vijay Varadharajan, Director of the ACS Computer Science Board and
Professor in Computing at Macquarie University, has indicated that as the demand for ICT
security professionals increases in the public and private sectors, there is a need for a method
of measurement to certify security professionals in terms of their qualifications and experience
Department
[Varadharajan 2004].
the
In 2003, ISIG released a discussion paper on the topic of certification. ISIG concluded that a
“national professional registry of information security professionals should be established in
by Communications,
consultation with Commonwealth and State Governments and industry organisations”.
Furthermore, ISIG suggested a “certification scheme should be integrated with the registration
process. That is to say, only persons who meet skills-based requirements should be
1982
registered under this scheme”. [Ames, Gaskell & Muir 2003]. ISIG suggested that the
necessary core components for the certification scheme should include:
Act
General knowledge of information security principles based on ISO/IEC AS/NZS
17799 and AS/NZS 7799.2; and
FOI Development,
General knowledge of Australian legal and regulatory requirements, including
state and federal laws, regulations, and standards [Ames, Gaskell & Muir 2003].
the
The development of a localised component for professional certifications has seen little
progress since it was recommended in the 2003 ISIG paper.
The Australian Computer Society (ACS) launched a bid in October 2004 to become the main
Regional
accreditation body for the Australian IT industry. In the launch the ACS argued for powers
under
similar to other industry organisations, such as the state bar association in the legal
profession [Jenkins 2005].
The Australian IT Security Forum (AITSF) has commented that the debate on information
security skills accreditation is still unresolved. AITSF and ISIG declared their joint position on
this topic in March 2005. Their position is characterised as follows:
Released Transport,
Page 9 of 98
IT Security Skills Accreditation in Australia
A multitude of (international) certification schemes for information security
professionals is already established.
An additional Australian scheme is neither desirable nor feasible.
We (AITSF) do not have a comprehensive picture of what the various
stakeholders expect from certification schemes.
We (AITSF) believe that the various stakeholders themselves do not have a
Arts
comprehensive picture of what to expect from certification schemes. [AITSF
2005]
the
2.4
INTERNATIONAL CONTEXT
and
Given the breadth of the field of information security, it is not surprising that there are differing
views on the required knowledge for a ‘professional’ in this area. Most agree that core
Infrastructure,
elements such as confidentiality, availability and integrity of information belong in the
of
discipline, while the inclusion of elements such as business continuity / disaster recovery
Sport
planning, insurance, fraud prevention and physical security of information assets and physical
documents have been questioned at times [ISPWG 2004].
While industry certifications have received criticism for their use of examinations as the
primary assessment mechanism, criticism has also been levelled at academic qualifications
for omitting a relevant work experience requirement. This element is seen by APEC as a
critical component of information security skills development. The APEC IT Skills Report
Department
tabled in 2004 states, “there is a role for APEC to ensure that IT skills development involves
an appropriate balance of theoretical and practical work” [APEC 2004].
the
According to a 2004 draft APEC e-Security skills report, of all APEC nations, only Japan has a
Communications,
national scheme specifically aimed at accrediting information security professionals. [APEC
by
2004].
In 2003, the European Information Society Group (EURIM) considered the training
requirements of law enforcement and industry in order to tackle e-crime. The EURIM report
1982
states, “only with formal accreditation are qualifications likely to be seen as having worth.”
[EURIM 2003].
Act
Following is a brief summary of international activity in the area of information security skills
accreditation
FOI Development,
2.4.1 Japan
the
Japan has implemented a number of schemes in the area of information security skills
accreditation, with each intended for a clear audience and use:
under Regional
Qualification Examination for Chief Telecommunications Engineers;
Network Information Security Manager (NISM);
Information Security Administrator Examination;
Qualification Test for Chief Evaluator of Security Target; and
Information Security Management System Auditor.
Released Transport,
[APEC 2004]
Page 10 of 98
IT Security Skills Accreditation in Australia
Japan implemented these schemes to encourage the alignment to international standards
(namely ISO/IEC 17799 and BS 7799.2). Subsequent to these schemes being put in place,
and claimed as evidence of the program’s success, 500 organisations have been certified
against these internationally recognised information security standards. [HKCS 2004]
2.4.2 United States of America
Arts
The US Government has not created its own certification scheme for information security
professionals. Instead, it requires individuals working in specific government information
the
security positions to obtain a commercially available information security certification
[Williamson, (ISC)2 2005].
For example, the US Department of Defence (DoD) is expected to issue an “implementing
and
manual” to accompany an existing DoD Directive, which will require approximately 110,000
Infrastructure,
DoD employees and contractors to obtain one of a number of specified commercially-
available information security certifications as a condition for their continued employment in
of Sport
information assurance and information management-related positions. The Directive
identifies six defined categories of personnel (Technical I, II and III; and Management I, II, and
III), with each position having a required level of certifications, with the accepted certifications
required to be ISO/IEC 17024 accredited [(ISC)2 2005c].
The US National Security Agency (NSA) and the US Department of Homeland Security (DHS)
have jointly developed a program to support the US National Policy on Critical Infrastructure
Protection (Presidential Decision Directive 63). The US National Centers of Academic
Department
Excellence in Information Assurance Education (CAEIAE) Program is responsible for the
accreditation of information security programs in academic institutions which have met the set
the
criteria [CAEIAE 2005].
by Communications,
There are currently 37 universities in the United States that meet the standards required for
recognition as CAEIAE [Fundaburk 2004]. Employers can then assess the capability of
individuals based on the course they have completed [APEC 2004]. However, Fundaburk
1982
indicates that skills and attributes taught in the curriculum of these Centers for Academic
Excellence had “no association with the skills and attributes employed, or addressed, by
information systems security professionals in an information systems security work
Act
environment” with the exception of Applications and Systems Development Security
[Fundaburk 2004].
FOI Development,
Hum Kim, Deputy Director for Policy and Strategic Initiatives at the Department of Homeland
Security’s National Cyber Security Division, has stated that, “The Department of Homeland
the
Security will encourage efforts that are needed to build foundations for the development of
security certification programs that will be broadly accepted by the public and private sectors.”
The National Security Agency (NSA) had special extensions developed for existing
Regional
certifications, including the CISSP Information Systems Security Engineering Professional
under
(CISSP-ISSEP) specialisation [Norris 2004].
The CISSP is a prerequisite for obtaining the Information Systems Security Engineering
Professional (CISSP-ISSEP) developed jointly between (ISC)2 and the US NSA. (ISC)2 has
also developed the Certification and Accreditation Professional (CAP) credential in
conjunction with the US Department of State. This credential is required for State Department
Released Transport,
employees who perform certification and accreditation functions within the Department
[Williamson, (ISC)2 2005].
Page 11 of 98
IT Security Skills Accreditation in Australia
2.4.3 United Kingdom
An independent study on the information security consulting industry provided for the UK
Department of Trade and Industry in 2002 highlighted issues surrounding practices and
qualifications in the industry. The Report’s findings included that due to the complexity and
rate of change in the knowledge base required for the industry, “the concept of information
security as a chartered profession is probably not yet relevant” [Sundt 2002].
Arts
With regard to qualifications, the Report found that current qualifications or accreditations
were “not considered as helping the information security services procurement process”.
the
Comments were made on the variable value of available qualifications, with those sponsored
by professional bodies generally held in higher esteem than commercially motivated
qualifications. Academic level qualifications were also generally held in high regard [Sundt
and
2002].
Infrastructure,
At the UK government level, the CESG Listed Adviser Scheme (CLAS) and the associated
Infosec Training Paths & Competencies (ITPC) Scheme oversees the practicing of information
of Sport
security, primarily in government, by providing professional membership and qualifications.
CLAS meets CESG’s very specific information security authority needs. The four variants of
the ITPC-administered Certificate of Infosec Competency awards are designed to certify
people from different levels of an organisation that implement UK government information
security policy and best practices [ITPC 2005].
The Institute of Internal Auditors (IIA) of UK and Ireland, a professional body, offers a
Department
Qualification in Computer Auditing (QiCA). The QiCA is specifically for the UK and Ireland and
the Institute does not offer a globally available alternative to the QiCA.
the
The Information Security Professionals Working Group (ISPWG) report on
The Institute for
Communications,
Information Security Professionals released in 2004 outlines a vision for a UK professional
by
body for information security, much in the same manner as other chartered professions
including engineers and accountants. An
Institute for Information Security Practitioners would
“provide Government and industry with highly professional practitioners in the field of
1982
information security, by providing a vehicle for members to demonstrate levels of judgment,
skill and competence in front of their own companies, peers and clients” [ISPWG 2004].
Act
At this stage, the field of information security certification is considered too young to allow for
meaningful comparisons of the success of these countries’ respective approaches. As such,
Development,
this information is best used to acknowledge the identification of the issue at an international
FOI
level, and the range of approaches being taken to move it forward.
the
under Regional
Released Transport,
Page 12 of 98
IT Security Skills Accreditation in Australia
3. THE CURRENT STATE
The current selection of information security skills accreditations available in Australia
includes professional certifications and academic degrees covering a range of knowledge
bases, from broad-based vendor-neutral certifications to vendor-specific and product-specific
Arts
offerings.
the
The review of the current state of play in information security skills accreditation in Australia
incorporates information on the range of available qualifications, along with their consideration
or positioning with respect to three key certifiable elements:
and
Knowledge
Infrastructure,
Experience
of Sport
Trustworthiness.
From the perspective of information security professionals, it is widely accepted that
marketability is the main driver for obtaining accreditation – the ability to gain access to
positions that would not otherwise be available without such a demonstration of competence.
3.1 AVAILABLE QUALIFICATIONS
Department
3.1.1 Academic Programs
the
A number of Australian universities offer postgraduate degrees in information security. Most of
by Communications,
the postgraduate courses offered are Masters Degrees with Graduate Certificate and
Graduate Diploma exit points. These courses extend for a period of one to three years on a
part-time workload, depending on the level of the degree or diploma. Fees are often
substantially higher than industry certifications; however, the Government does provide a fee
1982
assistance program for local students. Perth’s Murdoch University offers an undergraduate
Bachelor of Science in Internetworking and Security.
Act
A report tabled by the US PITAC (Presidential Information Technology Advisory Committee)
found that individuals providing and writing courses for universities may themselves be
FOI Development,
insufficiently qualified or knowledgeable. Some stakeholders in Australia hold the view that is
arguable point whether universities can train, certify or accredit at a better quality than
the
industry bodies.
University providers, see great value in their qualifications, crediting their longevity and their
capacity for teaching students the ability to learn. One end-user of such skills indicated that
under Regional
he holds tertiary IT qualifications in high regard. One tertiary provider noted that industry
certified professionals had sought university qualifications because they believed they did not
learn enough from passing an industry certification and required further knowledge
development. University programs attempt to give more industrial relevance to the material
covered by examining case studies and having guest industry lectures.
While academic qualifications in information security are well regarded by industry, it has
Released Transport,
been pointed out that most current IT security practitioners are unlikely to be willing to return
to academia to obtain a qualification.
Page 13 of 98
IT Security Skills Accreditation in Australia
3.1.2 Industry Programs
Judging by membership figures, the most popular broad-based certifications are
internationally recognised qualifications such as the Certified Information System Security
Professional (CISSP), Certified Information Systems Auditor (CISA), Certified Information
Security Manager (CISM) and Global Information Assurance Certification (GIAC).
At the time of writing this Report, there were 40,000 holders of the CISSP certification in 110
Arts
countries, with 600 of these based in Australia. CISA and CISM have a global base of
approximately 38,000 and 5,000 certified professionals respectively. In Australia, 76
the
professionals are certified with CISM, and within Oceania, there are 680 CISA certified IT
professionals. GIAC has 8,266 certified professionals internationally across a range of
certifications. The number of GIAC certified professionals based in Australia was not able to
and
be determined. In discussion with stakeholders, certifications such as those provided by
SANS, ISACA and (ISC)2 were generally well regarded.
Infrastructure,
The International Systems Security Professional Certification Scheme (ISSPCS) is a new
of Sport
international certification scheme developed in Australia by the University of Queensland,
Electronic Warfare Associates (EWA) and the Australian Computer Emergency Response
Team (AusCERT). The first class of professionals sat for the ISSPCS examination at the
AusCERT Asia Pacific Information Technology Security Conference in May 2005. The
ISSPCS certification is overseen by the International Systems Security Engineering
Association (ISSEA) which has hopes that the certification will offer “an international and
professional IT and Systems Security Certification Scheme that has wide credibility,
Department
jurisdiction and is genuinely international” [ISSPCS 2005]. Although developed in Australia,
the ISSPCS scheme is intended to be international in nature and does not focus on the
the
Australian marketplace. Currently more than 150 people have been granted ISSPCS
Communications,
Practitioner level certification or are in the process of being certified via the grandfathering
by
mechanism.
In Australia, information security professionals who wish to complete a defined set of
information security assessments for the Federal Government are required to attain the I-RAP
1982
certification developed by the Defence Signals Directorate (DSD) and SAI Global. The I-RAP
program currently has 34 members. I-RAP is a purely Australian certification program and it
Act
cannot be recognised internationally.
A second certification program focused on the Australian market is the ISIG Professional
FOI Development,
Membership level. In order to achieve this recognition, an information security professional
must be a member of ISIG, and must meet the following requirements. Professionals are
the
required to attain at least one of the following certifications: CISSP, CISM, CISA or I-RAP for
eligibility. As part of the application process, professionals must provide evidence of work
experience directly related to information security. Professionals must provide information
Regional
such as employer details, positions held, duration of the role and the security duties and
under
responsibilities assigned to the professional in that time. The onus is on the professional to
demonstrate four years of security-related experience, of which one year must be in Australia.
ISIG Professional Members are bound by the ISIG Code of Ethics which includes standards of
conduct regarding honesty, legal compliance, competence and diligence, professional
development and integrity. ISIG currently has 12 members at the Professional Membership
level, out of approximately 50 members. The Professional Membership status must be
Released Transport,
renewed annually.
Page 14 of 98
IT Security Skills Accreditation in Australia
In addition to the aforementioned industry and Government-supported certification schemes,
are the vendor and product-specific certifications, such as Microsoft’s Certified Systems
Engineer (MCSE) – Security, and Cisco’s Certified Security Professional (CCSP). Information
security professionals can obtain training for these certificates through a wide range of third
party training providers or can study for these certification exams independently. Vendor
certification examinations can generally be completed at national testing centres on an on-
demand basis. Vendors providing these courses were contacted for this project however the
Arts
number of professionals holding each of the vendor certifications could not be determined.
These industry supported certification programs were well regarded by the majority of
the
participants. For example, one consumer organisation indicated that all information security
staff in their organisation should hold or be working towards the CISSP certification. They
and
believed the broad-based CISSP satisfied 80 per cent of their organisation’s requirements.
The remaining 20 per cent was achieved through internal and self-learning, which were
Infrastructure,
actively encouraged by the organisation. The content of the CISM program was also viewed
favourably.
of Sport
3.1.3
Standards
ISO/IEC 17024-2004: Conformity Assessment – General requirements for bodies operating
certification of persons is an international standard developed with the objective of “achieving
and promoting a globally accepted benchmark for organisations operating certification bodies”
[SA 2004]. ISO/IEC 17024 states that a certification scheme should only be developed in
Department
response to specific government requirements or to a demonstrated market need or desire.
The scope of the standard identifies requirements for a certification body, including the
the
development and maintenance of a certification scheme for individuals.
by Communications,
The ISO/IEC 17024 standard is used as a method of measure for certifications in a number of
industry sectors. Certification bodies have been accredited under ISO/IEC 17024 for certifying
personnel and organisations against tasks such as Information Security Management
Systems (ISMS) auditing, project management training, and product inspection and testing. In
1982
the USA, organisations such as the Board of Safety Professionals, the National Board for
Certification in Occupational Therapy, and National Inspection Testing Certification
Act
Corporation are accredited with ISO/IEC 17024 [ANSI 2004a]. In the UK, organisations such
as the British Institute of Non-Destructive Testing, and the European Registration Scheme for
Development,
Personnel Competence are accredited with ISO/IEC 17024 [UKAS 2005]. As of April 2005,
FOI
JAS-ANZ, a joint accreditation body for Australia and New Zealand, required all certification
bodies under its scheme to comply with ISO/IEC 17024.
the
The ISO/IEC 17024 standard regulates the operation of certification bodies in three ways.
Firstly, the standard dictates the criteria for policies and procedures of a certification body.
Policies and procedures must observe fairness and equity among candidates; compliance to
under Regional
applicable regulations and statutory requirements; and the requirement for handling the
resolution of appeals and complaints from the public. Secondly, ISO/IEC 17024 defines the
structure of a certification body in order to ensure confidence in its competence, impartiality
and integrity. Thirdly, a committee is required to take responsibility for the development and
maintenance of the certification scheme. The certification body must prove it has the
necessary financial resources for operation of the certification system and ability to cover
Released Transport,
related liabilities.
Page 15 of 98
IT Security Skills Accreditation in Australia
Other areas addressed by the ISO/IEC 17024 standard include the requirements for:
Development and maintenance of a certification scheme;
A documented management system;
Monitoring of subcontractors in the certification system;
Maintenance of a record system;
Arts
Confidentiality of information gained and security of examinations;
The performance of resources, including examiners, employed by the certification
bodies; and
the
The re-certification process.
The ISO/IEC 17024 standard also recommends a job analysis be conducted at least every
and
five years to ensure that the certification scheme is still relevant to the role it certifies [SA
Infrastructure,
2004].
of
In June 2004, the American National Standards Institute (ANSI) accredited the CISSP
Sport
certification offered by (ISC)2 with ISO/IEC 17024 [ANSI 2004a]. In December 2004, the
Information Systems Audit and Control Association (ISACA) applied to ANSI for ISO/IEC
17024 accreditation of their CISA and CISM certifications, with this accreditation granted in
September 2005.
ISSPCS has also indicated that it is pursuing accreditation to this standard for its information
security skills certification program. (ISC)2 has indicated that they will be pursuing ISO 17024
Department
accreditation for a number of additional certification programs. ISSPCS noted that the use of
these ISO standards will assist in achieving convergence of standards in this area. It is
the
expected that this will then allow for a clearer differentiation based on content.
by Communications,
3.1.4 Certification Fees
Completing international certifications can be costly for Australian information security
professionals. This is largely due to high examination fees, followed by the requirement to re-
1982
certify at an additional cost after a period of time. In addition to the cost of the exam itself,
most certifications do not include training or materials as part of the certification fee. The
Act
following is a brief breakdown of costs for the most widely recognised certificates in industry.
Interviewed organisations seemed most familiar with the CISSP certification offered by (ISC)2.
FOI Development,
The standard cost for professionals wishing to complete CISSP certification is USD$599. A
discounted price of USD$499 is offered to professionals who register for the examination 16
the
days prior to the exam date. An annual maintenance fee of USD$85 is required.
ISACA offers two of the more recognised certificates in industry, CISA and CISM. The CISA
certification is priced at USD$460. The cost of the CISM certification is USD$455. The annual
under Regional
maintenance fee for CISA and CISM is the same. Certified ISACA members are required to
pay an annual maintenance fee of USD$40, while certified non-members are required to pay
USD$60.
The GIAC certificates offered by SANS have two distinguishable classifications, GIAC Silver
and GIAC Gold. The GIAC Silver certificate is the first step for candidates applying for
certification. Fees for GIAC Silver certificates range from USD$100 to USD$800, depending
Released Transport,
on the examination topic. Professionals are given the option of completing a GIAC Gold
certificate 18 months after attaining the GIAC Silver certificate. The application fee for a GIAC
Page 16 of 98
IT Security Skills Accreditation in Australia
Gold Certificate is USD$200. Depending on the certificate, re-certification is required every
two to four years.
The ISSPCS Practitioner level certification, developed by Queensland University of
Technology, AusCERT and Electronic Warfare Associates, has an examination fee of
AUD$500 plus taxes. Certification for the Practitioner level is valid for three years and re-
certification is AUD$300 plus taxes.
Arts
The I-RAP program is a mandatory qualification for professionals who wish to complete
specific security work for the Commonwealth. The application fee for I-RAP is AUD$275.
the
Registration for the I-RAP program costs AUD$2,200, and is followed by a mandatory training
and assessment fee of AUD$3,300. A maintenance training and assessment fee of
AUD$1,650 is required annually. A discount of 10 per cent off the standard price is offered to
and
members of AITSF.
Infrastructure,
Lastly, of the certifications examined, the least expensive qualifications are the vendor and
product-specific certifications. Prices for vendor certifications range from AUD$180 to
of Sport
approximately AUD$250. These include certifications from vendors such as CISCO, Microsoft,
Symantec and RSA.
Another choice available to Australian professionals is tertiary education. Australian students
at tertiary institutions have the advantage of receiving Government subsidies; however, due to
the duration of these programs and the inclusion of an ‘education’ component on top of a
‘certification’ component, the costs tend to be significantly higher. The following is a brief
breakdown of costs for courses offered by educational institutions in Australia.
Department
TAFE NSW offers an Advanced Diploma of Information Technology, specialising in e-security.
the
The cost for the Advanced Diploma is AUD$1,995. This course is available in New South
Wales, Victoria, and South Australia. The usual time of completion for this course is two years
by Communications,
and six months full-time.
RMIT University in Melbourne has a postgraduate degree in information security. The
program is divided into three stages, Graduate Certificate, Graduate Diploma, and Masters of
1982
Applied Science. The Masters is an incorporation of the Graduate Certificate and the
Graduate Diploma. The 2005 fees are AUD$4,800 for each stage of the program. The course
Act
is completed over a period of one-and-a-half years full-time or three years part-time.
The Queensland University of Technology offers a Graduate Certificate in Information
FOI Development,
Technology, specialising in information security. The fees per credit point quoted for 2005 are
AUD$100. A total of 48 credit points is expected for completion of the course, giving a fee for
the
the course of $4,800. Based on the completion of two units per semester, the course can be
completed in the space of 26 weeks.
Charles Sturt University offers a Masters of Information Systems Security over distance
Regional
education. The cost of this degree is AUD$2,100 per eight-point subject. Students are
under
expected to complete 96 points over the period of the course. Provided two subjects are taken
per trimester, students are expected to complete the course in two years.
The importance of ensuring the cost effectiveness of any new Australian scheme was
identified by many industry groups during the interview process.
Released Transport,
Page 17 of 98
IT Security Skills Accreditation in Australia
3.2 KNOWLEDGE
3.2.1 Body of Knowledge
Over the years, various organisations have developed independent bodies of knowledge for
information security certification. As a result, there are now a number of bodies of knowledge
in direct competition with each other. The following is a brief explanation of the international
Arts
bodies of knowledge studied by professionals undergoing various certifications.
The CISSP certification scheme is based on the Common Body of Knowledge (CBK). The
the
CBK is a compilation of material for information security professionals and comprises 10
security domains. These 10 domains are:
and
Access Control Systems and Methodology;
Infrastructure,
Applications and Systems Development;
of
Business Continuity Planning;
Sport
Cryptography;
Law, Investigation and Ethics;
Operations Security;
Physical Security;
Security Architecture and Models;
Department
Security Management Practices; and
Telecommunications, Network and Internet Security. [(ISC)2 2005a]
the
The CISA certification scheme is based on seven areas of knowledge and application. These
Communications,
areas are:
by
IS Audit Process;
Management, Planning and Organisation of IS;
1982
Technical Infrastructure and Operational Practices;
Protection of Information Assets;
Act
Disaster Recovery and Business Continuity;
Business Application System Development; and
FOI Development,
Business Process Evaluation and Risk Management. [ISACA 2005a]
The CISM body of knowledge is based on five job practice areas, defined from a job practice
the
analysis exercise intended to tie the material closely to the requirements of a practical
information security management role. These areas are:
Information Security Governance;
under Regional
Risk Management;
Information Security Program Management;
Information Security Management; and
Response Management [ISACA 2005b].
ISO/IEC 17799 is commonly confused as a certification available for individuals but it must be
Released Transport,
noted that ISO/IEC 17799 certification is only applicable to organisations.
Page 18 of 98
IT Security Skills Accreditation in Australia
At an international standard level, ISO/IEC 17799 has a body of knowledge comprising these
areas:
Security Policy;
Organisational Security;
Asset Classification and Control;
Personnel Security;
Arts
Physical and Environmental Security;
the
Communications and Operations Management;
Access Control;
System Development and Maintenance;
and
Business Continuity Management; and
Infrastructure,
Compliance [SA 2001].
of Sport
The Colloquium for Information Systems Security Education (CISSE) is an American
association established to serve as a “living body to bring government, industry and academia
together” in supporting the education of information security professionals [CISSE 2005].
CISSE’s predecessor, the National Security Telecommunications and Information Systems
Security Committee (NSTISSC) provides a body of knowledge in the standard for Information
Systems Security Professionals, NSTISSI 4011. The body of knowledge for NSTISSI 4011
covers areas such as:
Department
Communications Basics;
Automated Information Systems Basics;
the
Security Basics;
by Communications,
NSTISS Basics;
System Operating Environment;
NSTISS Planning and Management; and
1982
NSTISS Policies and Procedures.
The ISSPCS Practitioner certification scheme encompasses a Theoretical and Practical
Act
Knowledge Base (TPKB). The ISSPCS TPKB examines professionals on Security Processes
in relation to specific fields of application, called Functional Disciplines. The eight Security
FOI Development,
Processes identified are:
Strategic Security Management;
the
Compliance (Standards and Legal);
Asset Identification, Classification and Valuation;
Regional
Security Risk Analysis and Assessment;
under
Security Risk Treatment;
Operational Security Management; and
Security Operations for both Normal and Abnormal Conditions.
The six Functional Disciplines identified are:
Released Transport,
Fundamental Theory;
Environmental and Infrastructure Security;
Page 19 of 98
IT Security Skills Accreditation in Australia
Systems Security;
Communications and Network Security;
Physical Security; and
Personnel Security. [ISSPCS 2005]
Given the brief examples mentioned above, the overlap within the areas defined by the
various bodies of knowledge is apparent. However, there has been little work done to align
Arts
the certifications and standards in a comprehensive and meaningful skills framework. At
present, there are no in-depth skills measurements of existing certifications in the international
the
marketplace.
In June 2003, ISIG prepared a mapping of the CISSP and CISA certifications against the
and
ISO/IEC 17799 international standard. In the two years since this was completed, however,
the content for the CISSP certification has been revised to remove US-specific content, and
Infrastructure,
ISO/IEC 17799 is to be re-issued in 2005 with a new structure, resulting in the mapping no
longer being current. To support further development in this area, SIFT has provided initial
of Sport
mappings of the CISSP, CISM, CISA and ISSPCS Practitioner bodies of knowledge against
ISO/IEC 17799 in Appendix C to this Report.
3.2.1.1 Regionalisation
There is considerable debate about the amount, and level of Australian specific content that
needs to be developed and offered by the various certification providers. The consensus is
Department
however, that there is no need for a national scheme to serve this purpose.
The ISSPCS (Queensland University of Technology) academic board contends that the
the
current bodies of knowledge are too US-centric and have insufficient relevance for
Communications,
professionals in Australia and other regions including Asia and Europe. Others disagree with
by
this assessment, noting that the Law, Investigation and Ethics domain of the CISSP’s
Common Body of Knowledge (CBK) is only one of 10 areas and the one with the least
content.
1982
ISACA has indicated that the CISM certification is an international program and it does not
purport to offer any local or regional specific units. ISACA notes that while it could consider
Act
an Australian supplement for its certifications, it would need to ensure that equality was
maintained between regions. Its view was that industry should not have a hierarchy of
Development,
regions where the same certifications are ranked according to country of issue.
FOI
ISACA questions the need to regionalise, suggesting that the industry is heading towards
the
global standards. (ISC)2 has noted that its members have not indicated a requirement to have
an Australian IT security skills certification to demonstrate local knowledge. As the
marketability of certifications needs to be global an Australian certification would defeat that
purpose.
under Regional
A consumer/employer organisation noted that while the Australian technology experience is
identical to overseas experiences, the business and regulatory environments are very
different and experience in these areas is essential for good security execution in its sector.
Stephen Northcutt, Director SANS and GIAC, indicated that he believes Australian
components for international accreditation schemes are an important concept, and this is
Released Transport,
already being implemented within SANS with the MGT 512 courses run in Australia including
Australian legal components.
Page 20 of 98
IT Security Skills Accreditation in Australia
The ISIG Professional Membership category currently provides for regionalisation by requiring
at least one year of experience in the Australian information security market to be eligible.
The ISSPCS program was developed with the intent of meeting regionalisation needs but as
the program is new, regional components have not yet been developed.
From a law enforcement perspective, the Australian High Tech Crime Centre noted that
vendor and technology-specific qualifications, such as various RedHat, Microsoft and
Macintosh certifications, are valuable as these qualifications are recognised in court. As
Arts
these international qualifications are recognised in Australian courts, there is no real need for
a new accreditation scheme to serve this purpose.
the
One participant indicated that there is no single international qualification that can be relied
upon on which to base an ‘Australianised’ component.
and
The issue of regionalisation is dealt with in more detail in section 4.3 of this report.
Infrastructure,
3.2.1.2 Stratification
of Sport
All participants agreed that information security is an extremely broad discipline and it is
therefore not surprising that a number of certifications are now available in niche subject
areas, nor that broad certifications are moving towards specialisations. Examples of the
former include CISA (IS auditing) and GCFW (Firewall Analyst), and of the latter are the
CISSP:ISSAP (Architecture) and CISSP:ISSEP (Engineering).
Members of (ISC)2 have suggested extensions to the current range of certifications and
Department
consequently there have been moves to certify additional in-depth competencies beyond the
baseline credential. (ISC)2 has identified a need for additional competencies in areas such as
the
forensics, critical infrastructure protection, privacy, governance, risk management and
compliance.
by Communications,
While these specialisations are content-based, an alternative approach is for certifications to
be separated by ‘seniority.’ The ISSPCS certification scheme has proposed four levels, with
the first and only currently available level being the ISSPCS
Practitioner. This entry level is
1982
available to all ISSPCS applicants. The remaining three levels of ISSPSC certification are
Professional,
Mentor, and
Fellow. Progression to each level is dependant on successful
Act
completion of the previous level. It is understood that higher certification levels require a
greater involvement in the information security industry, along with an additional exam and
experience requirements as yet to be determined.
FOI Development,
ISIG, while supporting CISSP, CISA and CISM, recognises that current certifications are
the
struggling to keep up with the explosion in sub-disciplines within the industry. SANS
acknowledges that CISSP and GIAC certifications meet some but not all of the industry’s
needs. SANS is aware that there are many skills that current accreditations do not cover and
it is working to address this.
under Regional
One consumer/employer organisation suggested that while there currently existed a great
deal of knowledge and experience at the desktop this knowledge and experience diminished
along the hardware chain with mainframe expertise difficult to obtain.
Another provider indicated that students with management experience have attended their
programs to enhance their technical knowledge, particularly in cryptography and Public Key
Released Transport,
Infrastructure (PKI).
Page 21 of 98
IT Security Skills Accreditation in Australia
ISACA believes that management is far more relevant for a certification because of the
persistent nature of these skills. Therefore ISACA does not see a need to segment a
certification like CISM into different specialisations.
On the other hand, SAI Global believes there is a lack of management principles taught in the
current certification programs, suggesting that individuals in the industry generally come from
technical and network security backgrounds and lack an overall management perspective.
TAFE NSW has identified that there is poor alignment of technology with business objectives
Arts
in current programs and a lack of appreciation for business concepts.
the
One consumer/employer organisation identified a problem that managers were using broad-
based certifications to determine employee competence where specific niche skills were
required. In contrast, another consumer/employer organisation indicated that it placed little
and
emphasis on vendor (narrow) qualifications when recruiting information security professionals,
finding that individuals with a broad exposure to the information security body of knowledge
Infrastructure,
were more desirable.
of Sport
The industry is divided on the need for management level information security certification,
and the required content to provide an understanding of information security management
concepts in the existing certification programs. There is a greater degree of agreement
regarding the merits of both broad and narrow based information security certifications, with
the specific requirement depending on the organisation and requirements of the role. It is
expected that specialisations will be developed by certification vendors based on market
demand and will succeed where industry acknowledges the need and value.
Department
3.2.2 Assessment
the
The majority of the industry certification programs assess knowledge through an examination
by Communications,
conducted in person in university-level exam conditions.
CISSP examines professionals in all 10 security areas of the CBK in a six-hour examination
consisting of 250 multiple-choice questions. For CISA candidates must complete 200
1982
multiple-choice questions regarding the seven areas within the body of knowledge, in four
hours. For CISM, a similar requirement of 200 multiple-choice questions in relation to the five
Act
job practice areas applies, again over four hours. Candidates completing the ISSPCS
Practitioner certification are required to sit a four-hour examination. The I-RAP certification
scheme has a mandatory two-day training program and a written exam.
FOI Development,
A common criticism of existing certification programs requiring an exam-only assessment is
the
the failure of this method in validating the ability of individuals to practically apply knowledge.
Professor Bill Caelli, Head of the new School of Software Engineering and Data
Communications in the Faculty of Information Technology at the Queensland University of
Technology, has commented on the inadequacy of industry certifications in testing the
under Regional
competency of individuals and the ability to apply this in a real-world situation [Gray 2003].
The I-RAP program structure allows for an effective assessment of individual competence
with respect to the specific I-RAP audit tasks. The standards against which competence is
assessed are well known and structured, and as such it is easy to test the skills held by
applicants. I-RAP assessors use predefined checklists for completing audit tasks and these
checklists are returned to DSD upon completion. As a result, the DSD can complete an
Released Transport,
Page 22 of 98
IT Security Skills Accreditation in Australia
effective closed-loop assessment of competence, including a verification of the candidate’s
ability to apply the theory in a real-world audit scenario.
AusCERT and ISSPCS’s Academic Board indicate that evidence of continuing involvement in
the industry would be a good indicator of competence as there is a process of natural
selection. They noted that while a quantitative exam is the primary requirement at the
Practitioner level, higher levels will require mainly qualitative assessments.
Arts
A view was expressed by one participant that intensive short courses for certifications greatly
devalued these certifications with the net effect being that candidates holding a similar level of
the
certification have distinctly different underlying skill levels. While university courses are
expected to produce a more rounded and broadly applicable skill set, it may not be possible
for consumers of such services to distinguish between the two certified professionals.
and
ISSPCS indicated that there is a ‘Teaching Education Development Institute’ at the University
Infrastructure,
of Queensland which focuses on how individuals are assessed. The ISSPCS development
team has made extensive use of this group to ensure the exam approach and format
of Sport
accurately assesses an individual’s practical competence. Similarly, ISACA has a number of
groups that operate to ensure the ongoing standards of the program, including the Test
Enhancement Committee, the Certification Board and ISACA Governance. Certification
decisions are subjected to Board review on an annual basis to ensure close monitoring and
improvement of the process. (ISC)2 has a committee dedicated to the CBK from which the
(ISC)2 credentials are drawn, along with a Test Development Committee responsible for all
exam-related certification materials.
Department
3.2.3 Continuing Professional Education (CPE)
the
At present, all the main industry certification schemes in place in the Australian market require
by Communications,
some degree of continuing professional education, which contrasts with the majority of
academic programs which grant degrees and diplomas which do not have an ongoing
requirement.
1982
Consumer/employer organisations commented on the importance of up-to-date and relevant
knowledge.
Act
The value of CPE as currently implemented was questioned by a number of participants who
suggested that the CPE approach generally allows the certified individual to choose whether
FOI Development,
they want to undertake an ongoing education or simply meet minimum ongoing certification
requirements. ISACA and (ISC)2 conduct periodic audit checks to verify experience and
the
claims of CPE points, however these checks cover the range of activities across which CPE
points can be claimed, rather than the integrity of the process itself.
Under the GIAC program retesting is required to verify ongoing competence, but this is not a
Regional
popular approach.
under
It was agreed that effectively managed ongoing professional development was a necessity for
any Australian information security skills accreditation program.
Given the broad agreement on the importance of continuing professional development and
ensuring professionals maintain a suitable level of knowledge, alternatives to the existing
approaches to CPE and re-assessment need to be considered.
Released Transport,
Page 23 of 98
IT Security Skills Accreditation in Australia
3.3 TRUSTWORTHINESS
3.3.1 Trustworthiness and Professional Ethics
Many organisations have identified trustworthiness as the most important issue to consider for
a scheme, although it is acknowledged that trustworthiness is difficult to certify.
It was agreed that ultimately, staff trustworthiness checking has to be the responsibility of the
Arts
employer through due diligence, although it can be especially challenging for small to medium
sized organisations to gauge trustworthiness. Police checks are often inadequate in
the
determining the trustworthiness of a security professional; with an individual’s trustworthiness
judged only to the extent to which claims of previous experience are verifiable. It is however
and
difficult to verify ‘experience’ since most organisations will only state the duration of
employment and their rules do not allow them to report dismissal reasons. While it is
Infrastructure,
recognised that the due diligence process has high associated costs there is a necessary and
unavoidable level of due diligence required of a company’s management or human resources
of Sport
personnel in verifying experience.
The (ISC)2, ISACA and ISSPCS have codes of conduct and ethics that their certified
professionals are required to follow, however the related complaint mechanisms are not well
known and issues with certified professionals are often not reported.
ACS is working with CPA Australia and Engineers Australia to jointly accredit software
engineers, with these professional groups having the authority to revoke certifications. ACS
Department
has identified that in the information security space, voids are often filled by engineering and
accounting professionals, therefore the involvement of these groups is essential.
the Communications,
3.3.2 Professional Liability
by
The Professional Standards Council (PSC) allows professional bodies to apply for a scheme
to cap the liability of its members. In return, the bodies are required to have systems in place
1982
to regulate their members. With respect to an accreditation, the system must be able to
identify and administer suitable accreditations within the professional body.
Act
Each year, the professional body is required to report to the PSC on the strategy components
and key performance indicators of the system. Under the PSC scheme, professional bodies
must have insurance and liability disclosure. There is no direct contact between the PSC and
FOI Development,
the professional body’s members – it is the professional body which acts as the regulator of its
members.
the
The PSC scheme is created under the
Professional Standards Act 1994 (NSW) and the
Professional Standards Act 1997 (WA) and as such the relevant schemes are currently only
available within these jurisdictions. Most other Australian States and Territories are currently
under Regional
progressing legislation and programs to establish similar schemes with a view to achieving
national coverage.
Within this context, the ACS has proposed a two-tiered system for ICT professional
accreditation:
Using the Professional Standards Council program, the first tier will be a Certified
Released Transport,
ICT Professional accreditation, intended for consultants. These can have
Page 24 of 98
IT Security Skills Accreditation in Australia
specialist areas including security. To be a CICTP it will be necessary to provide
insurance details with this being subject to audit;
The second tier is a Practising ICT Professional, which does not require
professional indemnity insurance. However, it does require referees to gain entry
to this tier and an annual activity statement to verify CPE.
AITSF notes that while the PSC scheme may be useful in supporting smaller organisations,
Arts
liability provisions in contracts generally provide the structure around professional liability in
the IT security industry.
the
3.4 EXPERIENCE
and
Many organisations noted in discussions that the information security field was relatively
Infrastructure,
immature and as a result experience in this field is not yet a reliable indicator of competence.
In a field where demand for professionals outstrips supply, individuals are obtaining ‘credible’
of Sport
experience to attempt to demonstrate their capabilities but as participants noted time spent in
a position does not of itself demonstrate relevant capabilities.
Almost all of the certification schemes available to Australia require professionals to fulfil a set
of prerequisites before their application is accepted. A sample of the entry points for the more
common certifications completed by professionals follows:
The CISSP certification requires a minimum of four years of professional
Department
experience in the information security field, or three years plus a college degree.
Substitution for experience is allowed, with a Masters Degree in Information
the
Security from a National Centre of Excellence replacing one year towards the four-
Communications,
year requirement.
by
Professionals wishing to qualify for CISA certification must submit evidence of a
minimum of five years of professional IS audit, control or security work experience
to ISACA. The following exceptions are allowable:
1982
o
A maximum of one year of IS audit, control or security work experience may
be replaced by one full year of non-IS audit experience, or one full year of
Act
information systems experience, or an associate’s degree.
o
Two years of IS security audit, control or security experience work may be
FOI Development,
replaced by a bachelor’s degree.
o
One year of IS audit, control, or security experience may be replaced by
the
two years experience as a full-time university instructor in a related field,
such as computer science, accounting and IS auditing.
The CISM certification requires professionals to have a minimum of five years’
Regional
information security work experience, with a minimum of three years’ information
under
security management work experience in three or more of the job practice
analysis areas. Substitution is also allowable.
The ISSPCS certification requires professionals to have a minimum of three years’
work experience in information security, or a three-year IT-related degree
qualification. For grandfathering, a range of existing certifications can be used,
Released Transport,
such as a current CISSP, CISM, SANS GIAC GSE or an SSE-CMM Appraiser
certification. Applications are assessed by the academic board and reference
Page 25 of 98
IT Security Skills Accreditation in Australia
checks are conducted. With the University of Queensland as a key body,
academic qualifications are easily verified.
RMIT University accepts undergraduates in a scientific field or equivalent in its
master’s course. However, substitution is allowed at the discretion of the program
leader.
Charles Sturt University is similar in its prerequisites, requiring an undergraduate
degree or equivalent from students enrolling in its distance education course.
Arts
Queensland University of Technology requires an approved bachelor’s degree in
IT from a recognised tertiary institution with a point average of at least 4.5 on a
the
seven-point scale. QUT will also accept students who provide evidence of suitable
qualifications through a Recognised Prior Learning process, and significant full-
and
time IT work experience.
Infrastructure,
TAFE NSW permits people who have completed Year 12 or equivalent to enrol in
their Advanced Diploma course.
of Sport
The prerequisites for vendor-specific certifications vary but most, such as Cisco, Symantec
and RSA recommend before candidates apply for certification, but do not mandate, a
minimum period of experience with relevant product packages.
Alternatively, ISIG offers Professional Membership for those who are qualified with either
CISSP, CISM, CISA or I-RAP. Professional Members must have four years’ work experience
in an information security-related area, gained over the previous 10 years, with at least one of
the four years in Australia. A university degree may be substituted for two years of
Department
experience, and a higher degree or Graduate Diploma in information security may be
substituted for an additional one year of experience.
the
The pre-qualification requirements for joining I-RAP are:
by Communications,
i.
Evidence of current CISA certification and evidence of a minimum one year of
experience, gained within three years of the time of application, auditing information
security systems; or
1982
ii.
Evidence of current CISSP certification and evidence of a minimum one year of
experience, gained within three years of the time of application, auditing information
Act
security systems; or
iii.
Evidence of appropriate academic qualifications relating to information technology,
relevant to understanding information security systems and evidence of a minimum
FOI Development,
one year of experience, gained within three years of the time of application, auditing
information security systems; or
the
iv.
Evidence of a minimum two years’ experience, gained within three years of the time
of application, auditing information security systems.
A number of organisations have also noted that many quality information security
under Regional
professionals do not have degrees or certifications but have considerable experience. For
these professionals, there is often a lack of interest in obtaining a certification. Several
consumer/employer organisations indicated that qualifications are not a mandatory
requirement for recruitment as prior recruits, without qualifications but with experience, have
proved to be exceptional information security professionals.
Current ACS accreditations have a demonstrated equivalence process and a skills
Released Transport,
assessment process as additional entry points to their certification scheme. There is also a
Page 26 of 98
IT Security Skills Accreditation in Australia
‘senior manager’ pathway for people who have a demonstrated history of performance in the
area. At present, to validate experience, ACS requires individuals to provide certified
documentary evidence of their experience.
(ISC)2 observes that judgment improves with carefully managed experience and that
experience needs to extend beyond security skills to include general management, such as
budgeting, people skills, and presentation skills.
Arts
Given the choice of similar Australian or foreign experience most recruiters agreed they would
elect to employ the professional with Australian experience.
the
and
Infrastructure,
of Sport
Department
the
by Communications,
1982
Act
FOI Development,
the
under Regional
Released Transport,
Page 27 of 98
IT Security Skills Accreditation in Australia
4 THE NEED
Participants were given the opportunity to respond to the project’s investigation of the industry
need for a new Australian information security skills accreditation. Discussions were allowed
to range according to the interests and concerns of the participants and as such the issues
Arts
identified were not pre-determined by the interview process.
the
The needs identified by stakeholders and industry participants fell broadly into four categories:
the need for a mechanism to accurately assess competence;
and
the need for information security professionals to possess greater knowledge;
the need for professionals to possess knowledge and understanding specific to
Infrastructure,
the Australian business environment; and
of Sport
the need for an informed market.
In order to discern the need for an Australian information security accreditation scheme,
interview participants were asked what gaps existed in current accreditation schemes and
whether the implementation of a new Australian accreditation would supplement an
information security professional’s knowledge, trustworthiness, experience and competence at
an international level.
Department
The need for Australia to have its own accreditation scheme was questioned, with the
observation that an Australian information security skills accreditation could unnecessarily
increase the prices for information security services.
the
ESecurity Australia members have indicated that there is currently no customer requirement
by Communications,
for security professionals to be certified. They indicated that while they were content to obtain
relevant certifications as individual practitioners, they did not believe that
consumers/employers of information security services, particularly small organisations,
1982
required certified professionals. Members would not regard any requirement for certification of
information security professionals as significant in the improvement of quality in service. Large
Act
employers have indicated to members of eSecurity Australia that certifications are “nice to
have” rather than a ”must have” requirement for being retained to complete a security job..
It was noted that Australia already has access to certifications that work for the industry.
FOI Development,
However, if there were to be a new accreditation scheme it was important members said that
it be aligned with existing international standards to avoid creating a support structure.
the
Industry already has reference books and study materials for current information security skills
certification examinations. Any new Australian accreditation scheme could also devalue the
international certifications of existing professionals.
under Regional
Participants agreed that Australian information security skills needed to be accepted globally.
Information security is an export industry, allowing and requiring professionals to work
anywhere. As a result Australian professionals require global recognition for their skills and
qualifications.
It was suggested by some participants that the need for a scheme is an issue that has a wider
Released Transport,
application across the whole of the IT industry, and there would be benefits in leaving the
Page 28 of 98
IT Security Skills Accreditation in Australia
issue until a fuller review could be completed at the IT professional level before accreditation
for sub-specialisations should be addressed.
4.1 THE NEED FOR A MECHANISM TO ACCURATELY ASSESS
COMPETENCE
Arts
Many interview participants were interested in the role an Australian accreditation scheme
could play in promoting the image of information security professionals. Participants
the
recognised the need to regulate the industry and remove unreliable or untrustworthy
practitioners.
and
It was seen as essential that employers rely on commercial good sense in assessing the
competence of a professional i.e. technical interviews must be conducted with candidates if
Infrastructure,
technical knowledge is required. Of more importance is obtaining references from past
employers. Due diligence will always be essential.
of Sport
The difficulty in judging the competence and trustworthiness of information security
professionals based on their stated experience was recognised. Qualifications are valuable as
they indicate a degree of base knowledge and certification programs measure a level of
knowledge, establishing a benchmark for employers and interested third parties.
While large organisations generally have the experience, skills and current market knowledge
to recruit appropriately, it is difficult for small to medium enterprises to identify professionals
Department
with the right skills.
While some participants indicated that accredited security professionals have to date served
the
their clients well, others indicated that critical infrastructure operators do not believe current
by Communications,
certifications are meeting their needs, as they do not sufficiently guarantee the knowledge or
quality of an information security professional in a critical infrastructure environment. This is
particularly the case for industry sectors forming part of Australia’s critical infrastructure that
have not traditionally been online, such as transport, freight forwarding and water provision.
1982
It was suggested that there is a need to identify differences in the available bodies of
knowledge to provide a mapping of skills covered by each certification. Since no licensing or
Act
certification process will stop or capture the ‘cowboys’ in the market, industry should
investigate the possibility of expelling professionals from a certification scheme should they
FOI Development,
breach the codes of conduct and ethics.
One need identified by a critical infrastructure operator, was to ensure information security
the
knowledge fields were readily distinguishable, to support greater clarity around required
knowledge. For example, security practitioners, technical specialists and business continuity
managers are all in slightly different fields all under the broad title of information security.
under Regional
A participant highlighted the challenge of recruiting information security professionals who are
skilled in the full range of technologies, new and old such as mainframes and Unix. They
noted that current qualifications did not equip recruits fully for their information security roles.
They believed that text books were not teaching these information security topics adequately
and the theory of risk was not being translated into operational experience.
Other organisations did not enforce a requirement for a single certification in their recruitment
Released Transport,
process. Instead they first identified the skills required for a security role then sought the best
Page 29 of 98
IT Security Skills Accreditation in Australia
candidate, with some roles requiring vendor qualifications and others requiring business
experience.
The observation was made that there were many skilled people in the market without degrees
or certifications. One company emphasised the interview process to determine cultural fit,
knowledge and experience and said it was more inclined to consider certifications for
technical roles. This organisation said they would not place much emphasis on an Australian
information security skills accreditation scheme.
Arts
These varied experiences highlight the differences in recruitment practices between
the
organisations. Some organisations seek a single certification to provide a base level of
knowledge, whereas others take a more active role in defining knowledge requirements for
each specific position.
and
A representative from an information security and risk management-focused recruitment
Infrastructure,
organisation said there had been little demand from clients for candidates with formal
accreditation. Although certifications such as CISSP were regarded as a benchmark by
of Sport
practitioners in the industry, hands-on commercial experience was regarded as more
important to clients. It has been suggested that as the security market matures, more clients
will seek candidates with tertiary and professional accreditation as well as a level of
experience. Recruiters indicated that where candidates have similar skills and experience, the
deciding factor in the selection process would come down to qualifications.
Some organisations with specific needs have developed their own programs and initiatives,
designing a scheme to test and endorse professionals for their work requirements.
Department
A specific need in the market led to the development of the I-RAP program. The DSD had
the
identified a series of upcoming government initiatives, such as FedLink, which were expected
to increase the demand for DSD services. As such DSD anticipated the requirement for
by Communications,
suitably qualified professionals and it designed the I-RAP program to test and endorse
professionals for this work. The DSD requires these professionals to demonstrate their
knowledge of government information security policy and the I-RAP policies and procedures.
1982
Participants agreed that although there is an issue with assessing professional competence
within the industry, a new Australian information security skills accreditation program would
Act
not necessarily provide an ideal solution to the problem. Many agreed that current
certifications already have established a benchmark and an indication of base knowledge.
Similarly, many participants emphasised the importance of the interview process as an
FOI Development,
appropriate mechanism for assessing competence, rather than relying purely on professional
certification.
the
4.2 THE NEED FOR INFORMATION SECURITY PROFESSIONALS TO
under Regional
POSSESS GREATER KNOWLEDGE
In order to discern whether an Australian accreditation is required to fill the gaps in knowledge
of existing certifications, participants were asked to comment on how comprehensive current
certifications are in their coverage and examination of information security skills and
knowledge, and whether certified professionals possess the appropriate skills and knowledge
Released Transport,
to complete assigned tasks.
Page 30 of 98
IT Security Skills Accreditation in Australia
Many participants indicated that there was no need to change the current approach to vendor
and product-specific certifications, and that in these particular areas professionals have been
found to have the necessary skills to complete required tasks.
Others suggested that each role will have a required level of skills, experience and knowledge
and that the level of required knowledge should be defined and assessed as a part of
standard recruitment procedures. Organisations relied on different qualifications depending on
the role; for example, recruiting a broad-based qualified professional, such as CISSP, for
Arts
security management roles, and professionals with technical certifications for technical roles.
the
Some participants believed that there was a need for an ISO standards-based accreditation
model beyond overseas certifications such as CISSP and CISM.
and
Members of eSecurity Australia have faced challenges with the I-RAP program. According to
members of eSecurity Australia, I-RAP is regarded as too costly by some members to
Infrastructure,
undertake and some members feel that similar levels of systems audit skills could be
evidenced by an ISACA international systems audit certification. However as noted in the
of Sport
previous section of this report, the I-RAP program was designed to specifically incorporate
elements of government information security policy, rather than an attempt to create a
competitor to the existing certifications. As such, a comparison between I-RAP and
international certifications is only partially valid.
On the other hand, some experienced challenges with using existing certifications which did
not provide a broad education. One difficulty was the recruitment of professionals who have
the ability to develop business information security policies as well as a suitable technical
Department
background to understand the broader implications of policy issues.
the
In recognition of the changing needs of industry, ISACA evolved from a pure information
security (IS) audit organisation into an association covering IS audit, IT governance and
by Communications,
security. ISACA recently formed an alliance with ASIS and ISSA to help organisations
recognise the growing need for training in the Chief Security Officer (CSO) and Chief
Information Security Officer (CISO) roles. (ISC)2 has similarly created a ‘road map’ for the
1982
development of information security professionals into CISOs.
(ISC)2 has said that information security workers who do not seek to obtain and maintain
Act
professional status and competency are likely to remain under-skilled. Likewise, those who
may obtain certification within schemes that do not require continuing professional education
(CPE) are likely to become outdated in their skills.
FOI Development,
SANS similarly asserts that the biggest problem is currency with information security
the
professionals remaining under-skilled despite having qualifications. SANS does not believe
that the continual learning approach to certification is effective. SANS gives the example of
GIAC re-testing, which is not popular among members, as an alternative.
Regional
Most participants currently use certification as a means to determine the level of base
under
knowledge acquired by a professional. The issue does not seem to be the lack of essential
knowledge and skills taught by current certifications; in the rapid-paced information security
environment, participants were more concerned with the relevance and currency of
information security information taught by certifications. There was a need expressed for
certification bodies to maintain the relevance of certifications, together with a need for
information security professionals to pursue continual career development. The skill observed
Released Transport,
as lacking with most information security professionals, regardless of certification, was the
Page 31 of 98
IT Security Skills Accreditation in Australia
ability to understand both the business and the technical requirements of information security,
and developing security controls appropriately.
4.3 THE NEED FOR PROFESSIONALS TO POSSESS KNOWLEDGE AND
UNDERSTANDING SPECIFIC TO THE AUSTRALIAN BUSINESS MARKET
Arts
Interview participants were asked whether Australia needs its own accreditation to
compensate for cultural and/or content differences between Australia and other countries. The
the
majority response was that although there are regulatory and legislative differences between
Australia and other countries, that there is no need to create an accreditation scheme unique
to Australia. Participants also raised the issue of global limitation if Australia sought to
and
develop its own scheme.
Infrastructure,
Where a regionalised certification approach has been suggested, elements identified as being
region-specific include:
of Sport
Legal and regulatory environment.
Government standards such as ACSI 33.
Business environment and context.
Cultural issues.
Aligning technology with business objectives.
Department
Language.
Within government it was suggested that there is a need for professionals to have knowledge
the
of the Protective Security Manual (PSM), ACSI 33, and AS 4360, and this knowledge is not
Communications,
covered by existing certification programs. There may be a need for a ‘bridge’ to capture the
by
intricacies of the Australian environment over the top of international certification programs.
SANS members have indicated that professionals need to be able to demonstrate local
knowledge and an Australian IT security skills accreditation scheme could be a means to do
1982
this. In other countries, demonstrating regionalisation is also an issue for professionals. (ISC)2
has done ‘regionalisation’ work for the US Government, and is currently discussing
Act
arrangements with China, Canada, Singapore, the UK and a number of other countries.
Other participants indicated that the practical experience requirement of certifications was
FOI Development,
sufficient to ensure that a professional has the necessary work experience and had developed
the necessary social skills and environmental understanding to fulfil tasks as an information
the
security professional. For these requirements, Australian experience was no different from
experience gained overseas.
Concerns were expressed that although offerings from international providers were technically
under Regional
correct, there was a need for an overarching accreditation scheme which incorporated
Australia’s legal and regulatory context. For example, while the CISSP does not make
reference to Australian standards such as AS/NZS 7799 and AS/NZS 4360, the concepts are
included.
There was a divergence of participant’s opinion as to whether more than one standard for
information security skills certification was viable, with some participants suggesting that I-
Released Transport,
RAP should be adapted into a broader Australian certification scheme and others contending
that no single qualification could meet the breadth of industry need.
Page 32 of 98
IT Security Skills Accreditation in Australia
Participants were also divided on whether or not an Australian content was required. While
some felt that it was important to have an understanding of the Australian environment, others
maintained that the practice of security principles only differed slightly on an international
scale. However, it should be acknowledged that the level of knowledge and understanding
required of an information security professional is also dependent on the nature of the
organisation and the role of the professional. For example, while it is important for a
professional working in a Government agency to be aware of the PSM, or the ACSI 33
Arts
standard, it may be more relevant for a professional working in the telecommunications
industry to understand implications of Australian telecommunications interception laws.
the
4.3.1 Requirement for local legal & regulatory knowledge
and
The requirement for information security professionals to have knowledge of the Australian
legal and regulatory environment was an area subject to considerable discussion by
Infrastructure,
participants. While there was an in-principle consensus that this knowledge is worthwhile,
of Sport
there was disagreement as to whether this should be a mandatory component of a
certification program rather than merely an additional element of knowledge to be considered
when selecting an information security professional.
One view expressed was that Information and Communications Technology (ICT)
professionals needed to have a good understanding of the legal and regulatory environment
in Australia. It was suggested that some overseas professionals cannot fit into the culture of
Australian organisations as they have a different understanding of ethics and regulations. It
Department
was noted that the issue of regionalisation is also faced by other professions, such as the
legal sector where of foreign lawyers are required to complete bridging courses before being
the
allowed to practice in Australia.
by Communications,
Other participants acknowledged the need for professionals to understand privacy and
surveillance laws in Australia, but saw it is an organisation’s responsibility to educate their
employees about boundaries. Participants believed that information security professionals
should not be expected to know the legislative differences.
1982
Some Australian ICT companies have had issues with legal compliance in the past; eg,
providers of IT services might be operating appropriately according to US law but might be
Act
violating telecommunications interception laws in Australia. As legislation changes, there may
be a need for a professional organisation to ensure continuing education in this area.
FOI Development,
Both small business representatives and larger companies indicated that it is necessary for
Australian information security personnel to understand the Australian legal and regulatory
the
environment, however participants differed in their views as to who should provide this
knowledge.
Some organisations have business units within the organisation responsible for ensuring
under Regional
regulatory compliance, but nonetheless would value information security professionals having
knowledge of the telecommunications industry as well as Australian legal and regulatory
knowledge.
The legal and regulatory knowledge required of professionals varied depending on the
participant’s industry sector. The majority of participants agreed that it was important for
information security professionals to have an understanding and awareness of Australia’s
Released Transport,
legal and regulatory environment in order to practise information security within legal
Page 33 of 98
IT Security Skills Accreditation in Australia
boundaries. However, participants did not view an Australian information security skills
accreditation scheme as a solution to this problem.
4.3.2 Appropriateness of information security professionals providing legal &
regulatory advice
In addition strong views were expressed by some groups as to the appropriateness of
Arts
information security professionals providing legal and regulatory advice to their clients.
Participants agreed that although it was beneficial for an information security professional to
the
have knowledge of legal and regulatory issues, organisations should not be turning to
information security professionals for legal or regulatory advice.
and
4.3.3 Extent of required regionalisation
Infrastructure,
Participants were questioned on the extent to which current certifications should be
regionalised to cater for information security professionals practising in Australia.
of Sport
It was noted that many Australian companies are subsidiaries or parent companies of
companies in the US, Europe or Asia, and the laws of those jurisdictions must be taken into
account. International legal and regulatory frameworks are often relevant to Australia, with
legislation such as Sarbanes-Oxley and the European Privacy Directive having an impact on
Australian companies operating internationally. However, participants noted that legislation
between states often differed, for example privacy legislation.
Department
Providers advised that for regionalisation to be offered there needed to be clearly defined
boundaries and jurisdictions within relevant regulatory regimes. Participants also observed
the
that individual professionals shared part of an organisation’s responsibility for compliance.
by Communications,
4.3.4 Maintaining international relevance
Participants questioned the validity and quality of its benefits on a global scale of an
1982
Australian information security skills accreditation program. Participants were concerned that
Australia would be removing itself further from a field that increasingly required professionals
to work on a global scale, regardless of geographic boundaries.
Act
Standards Australia believes there is no need for a uniquely Australian scheme as it would
require global recognition. It would also be necessary to ensure that any new scheme was
FOI Development,
not a restraints to trade. Standards Australia does accept the need for knowledge of
Australian regulation and legislation in order for information security professionals to complete
the
their responsibilities in the market, but deems it sufficient to have Australianised components
extended from international accreditation schemes to cover this need.
It was considered important to have access to internationally recognised schemes with more
under Regional
frequent course offerings, and a greater recognition of the value of information security skills
accreditation. The information security industry itself is heading towards global standards.
Australian professionals require global acceptance and marketability on a global level.
(ISC)2 agrees that in many instances a solid understanding of Australian regulation would be
needed. Most likely it would also require international accreditation to meet the needs of
increasingly internationalised commerce, due to the proliferation of multinational corporations
Released Transport,
and international cooperation among governments.
Page 34 of 98
IT Security Skills Accreditation in Australia
Consensus from participants was that an Australian information security skills accreditation
program would be worthwhile only if it could achieve recognition and acceptance on an
international level. The majority of participants at interview were satisfied with the current
offerings of certifications recognised by organisations based in Australia, as these are
internationally ‘portable’.
Arts
4.4 THE NEED FOR AN INFORMED MARKET
the
4.4.1 Content & relevance of certifications
In order to determine if an Australian accreditation program is necessary to provide relevant
and
information to professionals practising in Australia, participants were questioned on the
adequacy of content and relevance of the certifications available to Australia.
Infrastructure,
The consensus was that for critical infrastructure operators a framework of accreditations is
of Sport
needed that match required skill needs. There are currently multiple certificates with different
values available to an uninformed market. Industry needs a mechanism to understand what
current certificates imply. From a consumer/employer’s perspective the challenge is to
understand what information security services they are buying. It was considered that
Australia does not need to adapt existing programs or create new programs as there are
already too many in existence.
There was a belief expressed that more work needed to be done to assist SMEs appreciate
Department
their need for information security. Non-technical business operators expect to employ IT
staff or contract IT resources who have an understanding of their organisation’s broad needs
the
and security requirements. Many employers are ignorant of IT accreditations in general and
Communications,
are certainly unaware of accreditations for information security professionals. .
by
The major issue with the current qualifications noted by participants was not the lack of
relevant content or knowledge; rather it was the lack of understanding by employers as to
1982
what the qualifications offered. Participants admitted difficulty in distinguishing the skills
examined by the various qualifications and proposed that the mapping of skills to
qualifications would be of more assistance than the creation of a new accreditation scheme.
Act
4.4.2 Membership of programs
FOI Development,
Industry groups and representatives also observed that it was difficult to distinguish if
professionals were certified, and that certification did not necessarily equal quality or
the
competence.
Since it is not commonly known who is certified and who is not, referees are very important. It
Regional
was suggested that there should be more openness about who is certified and better use of
under
certification providers’ ethics and complaints processes to assure this.
While most international certifications have an enforced Code of Ethics mechanism,
participants noted that it was unlikely that many people would report complaints back to (ISC)2
and ISACA. ISIG has suggested localisation in this area to provide improved assurance.
It is expected that as information security skills accreditation awareness grows, there will be a
Released Transport,
similar growth in the use of these credentials by professionals to differentiate themselves. It is
known that at least some of the certification providers have searchable online databases of
Page 35 of 98
IT Security Skills Accreditation in Australia
certified professionals, and increasing the awareness of these facilities is expected to support
the verification of membership and willingness to report ethics breaches back to providers.
4.4.3 Due diligence requirements
Participants believed that there were common misunderstandings about an organisation’s
responsibility to due diligence when engaging any professional. A professional’s achievement
Arts
of certification should not be seen by organisations as a replacement for due diligence in the
form of background checks and thorough interviews.
the
A need was identified to educate employers about what constitutes due diligence. It was
proposed that consumers/employers of these professionals needed to clearly define their
requirements in a concise manner identifying the set of skills and knowledge they expect
and
information security professionals to possess.
Infrastructure,
There is no suggestion that this issue is unique to the information security industry. In all
of
industries there is a need to ensure that a given candidate for a role is technically competent,
Sport
possesses the required knowledge, will be a cultural fit, and has the necessary integrity for the
position. Certification programs have a limited capacity to meet these requirements.
Department
the
by Communications,
1982
Act
FOI Development,
the
under Regional
Released Transport,
Page 36 of 98
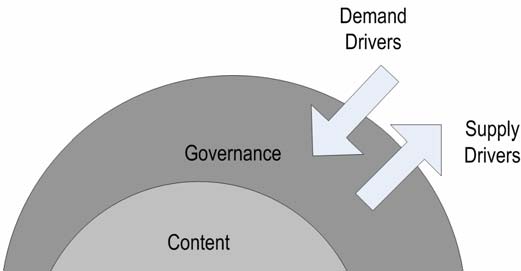
 5 THE WAY FORWARD
5 THE WAY FORWARD
On the 15 June 2005, a workshop with key stakeholders and interested parties in the
information security industry was held to present the initial findings of SIFT Pty Ltd on the
current state of information security skills accreditation in Australia and to provide a forum for
Arts
discussion on the issues identified by the initial findings. The objective of the workshop was
to identify an acceptable ‘way forward’ for the industry on the issue of information security
the
skills accreditation in Australia. The workshop was structured into three presentations
Report on the Current State,
and
Report on the Need, and
Infrastructure,
Models and Options.
of
Each presentation was followed by an open discussion with workshop participants. The
Sport
following sections detail observations of workshop participants in relation to the findings
presented by the consultants.
5.1 CONTEXT OF OPTIONS
Department
5.1.1 Elements of a Successful Program
Workshop participants were presented with the following diagram which illustrated the key
the
elements for achieving a functioning model for information security skills accreditation in
Communications,
Australia.
by
1982
Act
FOI Development,
the
under Regional
Released Transport,
Figure 1: Elements of a successful accreditation program
IT Security Skills Accreditation in Australia
Definitions of each of the broad elements are included below.
5.1.1.1 Generally accepted requirements & principles
A number of fundamental requirements were identified and remained consistent throughout
discussions with a wide range of organisations including information security professional
service providers, consumers, representative bodies, and end-users.
Arts
5.1.1.2 Content
Issues surrounding the contents of the body of knowledge required by an information or IT
the
security professional, along with discussion on the need for specialisation and regionalisation
of certifications were discussed.
and
5.1.1.3 Governance
Infrastructure,
In examining the governance aspects of a way forward, the full range of alternatives – from a
of Sport
laissez-faire market forces approach to a prescriptive licensing requirement were canvassed.
5.1.1.4 Demand and supply drivers
In order for any Australian scheme to succeed, it would be necessary to identify drivers and
impediments to adoption both for providers and consumers/employers of information security
professional services.
Department
5.2 GENERALLY ACCEPTED PRINCIPLES
the
When discussing the way forward with stakeholders and interested parties in the initial phase
by Communications,
of this project, a number of items were identified as requirements, principles, or ‘boundaries’
on approaches that would receive industry support. Workshop participants were presented
with the following headings which sought to capture these principles and requirements.
1982
5.2.1
Do not ‘re-invent the wheel’
Act
The vast majority of organisations interviewed agreed that any Australian scheme should build
on the work completed by existing certification programs rather than ‘re-inventing the wheel’.
FOI Development,
Workshop participants agreed that industry should not look at creating a solution based on a
new body of knowledge. The solution should build upon knowledge already available from
the
current schemes.
5.2.2
Provide an open standard
under Regional
Many industry professionals have already obtained well-recognised international certifications,
and in order to maintain industry support, it was necessary to provide for these certifications to
be recognised within any new information security skills accreditation scheme. Similarly, it
was necessary to provide for industry certifications and academic qualifications to co-exist.
Workshop participants agreed that the agreed solution must be inclusive of programs already
Released Transport,
in existence, including existing certifications, along with tertiary education degrees and
diplomas.
Page 38 of 98
IT Security Skills Accreditation in Australia
5.2.3
Minimise financial impediments
To ensure wide acceptance and use, any new scheme must provide value for money. This
principle also extended to ensuring it was not necessary to join a large number of schemes to
ensure ‘coverage’ of the information security skills arena.
Workshop participants agreed that the cost of developing and maintaining a solution should
not create a barrier to the participation and contribution of IT security professionals.
Arts
5.2.4
Maintain vendor neutrality
the
It is accepted that a each vendor is in the best position to define the knowledge requirements
for its own products. For the purpose of broad information security skills accreditation, it was
and
proposed that any certification should be vendor-neutral, although broad platform-specific (ie.
Windows, Unix/Linux) knowledge would remain important and relevant.
Infrastructure,
Workshop participants agreed that the solution should not focus on specific vendor products
of Sport
and solutions but should maintain an awareness of the importance of vendor engagement.
5.2.5
Achieve industry acceptance
Regardless of the chosen way forward, industry acceptance would be essential, both by
providers and consumers/employers of information security professional services.
Workshop participants agreed that industry must be willing to own and sponsor any agreed
Department
new approach in order to maintain relevance and reputation in the market.
the
5.2.6
Maintain international relevance
by Communications,
Any scheme proposed would need to be internationally recognised, portable, and relevant.
Workshop participants agreed that the solution should not restrict Australian information
security professionals from practising on a global scale, nor should it limit the ability of
1982
international professionals to practise in Australia.
Act
5.2.7
Continued requirement for due diligence
Certifications do not relieve an employer of their requirement for due diligence in assessing
FOI Development,
the suitability of a professional for a particular role.
the
Workshop participants agreed that the solution must not be seen as a replacement for
organisational due diligence when selecting a suitable candidate for an information security
role.
under Regional
5.3 CONTENT
One of the items generating the greatest discussion with stakeholders and industry
participants was the selection of the body of knowledge to be used for either an Australian
scheme, or for a gap analysis of existing schemes. The fundamental question was what the
Released Transport,
required knowledge base was for an information security professional operating in Australia,
and on this point there is considerable divergence of opinion.
Page 39 of 98
IT Security Skills Accreditation in Australia
5.3.1 Basis
During the initial interview phase of this project some participants suggested that ISO/IEC
17799, and AS/NZS 7799.2 could provide an appropriate body of knowledge on which a body
of knowledge could be standardised, particularly as these standards were recognised by
Government. However, it was noted that existing bodies of knowledge in certifications such
as the CISSP in no way stated requirements contrary to the application of the Australian
standards.
Arts
Another alternative suggested was the body of knowledge created by the National Security
the
Telecommunications and Information Systems Security Committee of the US National
Security Agency, as the curriculum established by this group has been used in the
establishment of a number of other bodies of knowledge.
and
At the workshop, SIFT presented the option of basing the content of the solution on one of the
Infrastructure,
following: ISO 17799, AS/NZS 7799.2, CISSP CBK or NSTISSC 4011. Discussion led to an
understanding that there could be no agreement on a ‘body of knowledge until job skills within
of Sport
information security had been identified.
5.3.2 Developing Regional Knowledge
In the initial interview phase, certification bodies were asked if there was any intention of
‘regionalising’ current certifications available to Australia.
(ISC)2 was uncertain whether a regionalisation of the CISSP program would be financially
Department
viable in Australia but said it would be both more effective and economic to use existing
internationally accredited certification schemes than to develop a new scheme from the
the
ground up.
by Communications,
A director of SANS and GIAC, noted they would be happy to work with the industry to
regionalise existing certifications if there was a committed level of training/certification seats
per year.
1982
Industry groups and representatives were asked what the ideal method of integrating regional
knowledge was for information security professionals. Both small business representatives
Act
and larger companies agreed that extending international accreditation schemes to
incorporate required Australian components was preferable to developing a new Australian
scheme from the ground up.
FOI Development,
5.3.3 Stratification of Certifications
the
Due to the breadth of the information and IT security industries, broad certifications are now
moving to specialisations and other mechanisms to ‘stratify’ the membership. Various levels
Regional
have been proposed for such stratification, including:
under
Industry (eg, banking & finance, telecommunications, government)
Management/technical focus
Job role (eg, architect)
Required skill set (eg, investigations).
Released Transport,
In addition to this, it was suggested that certification and professional association membership
should occur at the broad ICT industry level rather than for specialisations such as security.
Page 40 of 98
IT Security Skills Accreditation in Australia
The approach to having ICT industry level professionalism and certifications (as opposed to
moving directly to a security specialisation) was proposed by some participants on the basis
that resolving the broader professionalism question before moving to specialist areas could
improve the end result.
It was noted that any Australian certification or accreditation scheme would require
contextualisation based on the industry to which it related. For example, critical infrastructure
organisations were more likely to require an additional degree of knowledge or background
Arts
checks.
the
(ISC)2 indicated that additional competencies that may require certification include forensics,
critical infrastructure protection, privacy, governance, risk management and compliance.
SANS and GIAC similarly indicated that current programs were “only scratching the surface”
and
of available competency areas. Such comments suggest that over time there will be an
increase in the number of certifications available and the scope of roles covered by such
Infrastructure,
certifications.
of Sport
Workshop participants observed that a clearer understanding was needed within the market of
the available roles in information and IT security, and the necessary skills that match each
role. Certification was seen to fit in through providing an assurance of a baseline level of
knowledge for specific skills that would match identified specific roles.
5.3.4 Re-certification and continuing professional education (CPE)
Department
During the initial interview phase, participants were asked for their views on the need to
incorporate re-certification and continuing professional education as part of the solution.
the
Participants noted that while the continuing professional education of personnel in appropriate
Communications,
legal and regulatory issues may be a requirement, they differed in their views of whether CPE
by
should be a requirement of ongoing certification.
(ISC)2 suggested that such mandated CPE credits would be appropriate where a certification
1982
program was developed with localisation in mind but would be inappropriate for the
international programs. Others noted that given the immaturity of the field, mandating certain
areas of CPE study (eg, legal and regulatory) would not be recommended.
Act
Workshop participants were neutral with regards to the issue of re-certification and offered no
additional comments.
FOI Development,
5.3.5 Trustworthiness and clearances
the
Many organisations identified the issue of trustworthiness as one of the key challenges in the
information security marketplace, but an equal number indicated that this is not the
Regional
responsibility of a certification program.
under
It was suggested that due to the small size of the information security industry in Australia, it
could be feasible to establish a “web of trust” where a series of referrals could provide a
suitable approach to trustworthiness. Such an approach could utilise a board panel of review,
and supervisor’s reports for completed projects. It is acknowledged, however, that such an
approach would have considerable confidentiality implications and administrative overheads.
Released Transport,
Page 41 of 98
IT Security Skills Accreditation in Australia
It was noted as the information security profession in Australia was small and, particularly for
senior roles, the network of professionals is very good, allowing for a suitable degree of
competence and trustworthiness assessment based on trusted referees was a feasible
concept.
It was proposed that the development of a ‘personnel security’ standard could ease the
difficulty many organisations face in determining what checks can and should be conducted.
Standards Australia confirmed that it was considering the issue of background checks but did
Arts
not have definitive view at this stage.
the
A certification for trustworthiness could be considered, similar to models in the US where
individuals can submit themselves to an independent board for vetting.
and
Through further discussion it was determined that the issue of ‘standardised’ clearances
related to support for organisations in undertaking due diligence on personnel for key roles.
Infrastructure,
of Sport
Department
the
by Communications,
1982
Act
FOI Development,
the
under Regional
Released Transport,
Page 42 of 98
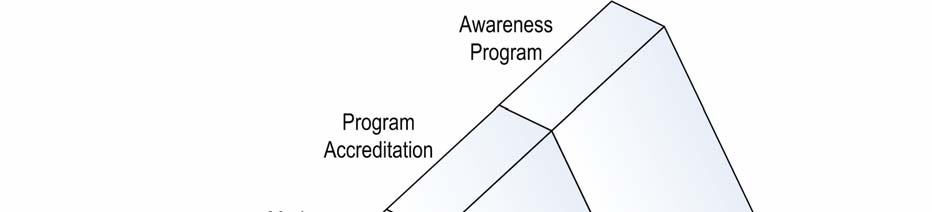
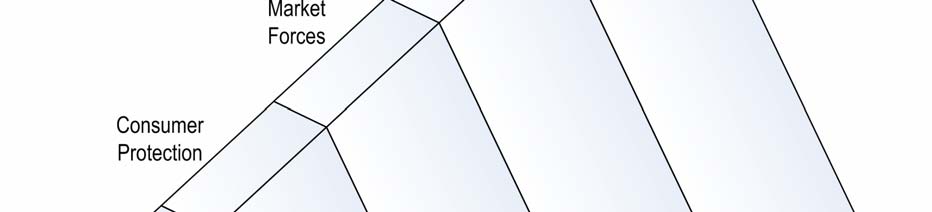
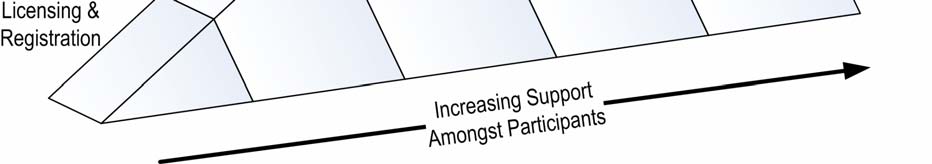
IT Security Skills Accreditation in Australia
5.4 PROPOSED APPROACHES
5.4.1. Degree of Support
Workshop participants were presented with the following diagram of the possible approaches
and the respective levels of support across the industry.
Arts
the
and
Infrastructure,
of Sport
Department
the
by Communications,
1982
Figure 2: Proposed approaches and levels of industry support
Act
Participants indicated a strong belief that one of the primary issues in the market was a lack of
FOI Development,
understanding of the relevance of the existing certification programs to different industries, job
roles and technical and business environments. As a result, there was considerable support
within Government, professional bodies and large and small private sector organisations for
the
an awareness program to provide clarity for consumers/employers/end-users.
Based on the interviews conducted and the workshop discussion there is very little support
Regional
within industry, either from the information security professional service providers, or from the
under
end-users of such services for a mandatory licensing or registration scheme of any kind.
Some participants had the view that given the immaturity of the information security skills
market certification is best left to market forces at this stag.
Other participants suggested a ‘program accreditation’ structure to provide for the
maintenance of consistent standards between competing certification schemes. Such a
Released Transport,
program accreditation, also described by some as a ‘meta-certification’, itself has many
variables in its implementation, such as the need for a governing body (and if required, the
Page 43 of 98
IT Security Skills Accreditation in Australia
identity of such a body), and any additional requirements placed on top of the need to simply
obtain an accredited certification. Such requirements were generally suggested to include
elements of regionalisation, optional specialisation and detailed ongoing industry involvement
and continuing education requirements.
The final broad category of suggested governance structures was for the use of existing, or
refined, consumer protection mechanisms to improve the quality and consistency of services
in the area of information security.
Arts
There was consensus among workshop participants that the relative acceptance levels of the
the
five approaches were indicated correctly, with the awareness program deemed as most
appropriate to requirements. Participants at the workshop also agreed that an Australian
information security skills accreditation scheme was not an acceptable solution for the needs
and
of industry and the marketplace.
Infrastructure,
5.4.2. Licensing and Registration
of Sport
It was suggested that a licensing and/or registration program should be put in place for
information security professionals, particularly those working with safety critical systems.
However, the vast majority of organisations interviewed during the project were strongly
opposed to any attempt to mandate a specific scheme or to create any form of prescriptive
regulation in the information or information security skills markets.
As participants clearly indicated that such a scheme would not receive market support either
Department
from suppliers or consumers of information security professional services, it was
recommended that this not be further considered.
the
Workshop participants were not supportive of the licensing and registration model for a
by Communications,
solution.
5.4.3. Consumer Protection
1982
As one of the drivers identified for the information security skills accreditation program was the
need to ensure small to medium enterprises were receiving quality services, it was proposed
Act
that standard employment contracts could be used to provide some consistency.
It was suggested that some participants that consumer law could afford some level of
FOI Development,
protection for SMEs acquiring information security services. There was however agreement
that standard employment contracts alone could not ensure that professionals were able to
the
meet individual organisation’s requirements.
It was similarly noted that the utility of consumer protection mechanisms such as standard
form contracts was minimal as the large consumers/employers of information security
under Regional
professional services will generally use internal legal and compliance personnel and
associated contracts.
5.4.4. Market Forces
A number of interview participants made the point that allowing market forces to dictate the
Released Transport,
direction of accreditation and certification is an important alternative to consider.
Page 44 of 98
IT Security Skills Accreditation in Australia
A number of organisations suggested that many of the issues being discussed were ‘growing
pains’ as the information security field matured. As standard practices and procedures were
put in place, and as a better understanding of professionalism in this context was developed,
the accreditation/certification issues would be resolved.
Many users of information security professional services indicated that they do not enforce a
requirement for qualifications in the field, as unqualified practitioners have often proved to be
exceptional information security professionals. It is expected that irrespective of the
Arts
establishment of a new certification/accreditation scheme, companies would continue to
recruit personnel outside of this scheme where they were considered to be the best
the
candidate.
Organisations have identified that university graduates with certifications often lack practical
and
and operational experience. However, it was felt that this analysis of practical and operational
experience would be handled through existing recruitment and interview processes, rather
Infrastructure,
than attempting to use a certification program for this purpose.
of Sport
(ISC)2 noted that current market needs have generated several internationally recognised
information security personnel certifications and future needs were currently generating the
development of others. TAFE NSW similarly indicated that it was often better to maintain an
‘open’ approach to standards and to allow the market to fill the need.
AITSF said that from an information security industry perspective, its preferred option would
be to let the market decide, and that most organisations were happy with the international
certifications available.
Department
The reaction from the workshop towards market forces driving the solution was very positive.
the
It was noted by participants that a demonstrated amount of information and effort has been
contributed to current information security skills accreditation by market forces. The identified
by Communications,
opportunity would be to supplement market forces to achieve a degree of consistency and
maturity in the information security marketplace sooner than would otherwise be achieved.
1982
5.4.5. Program Accreditation
During the interview phase of the project, there was considerable discussion around the
Act
relative benefits of certifying individuals, or accrediting certification providers. It was believed
that that quality could be assured through a board or council providing accreditation of the
FOI Development,
program itself.
It was proposed that an accreditation (umbrella) organisation could be established utilising a
the
JAS-ANZ-type accreditation process, with the certification bodies underneath, thus providing
assurance of the certification process. Since accrediting certification bodies would be likely to
be process-intensive, it would be necessary to demonstrate significant value for the certifying
Regional
organisations to get them on board. However, not all participants agreed with this proposal.
under
Participants questioned the benefits of having an additional level of bureaucracy.
It was agreed that ‘unification’ of existing certifications into a single Australian scheme is
unlikely, both due to the commercial drivers of the certification bodies and the needs of
specific areas of the industry. For example, it is expected that DSD will continue to operate
the I-RAP program regardless of other programs put in place, due to the nature of the work
Released Transport,
and Government control of the relevant standards (ACSI 33 and the Protective Security
Manual).
Page 45 of 98
IT Security Skills Accreditation in Australia
As the “program accreditation” approach has the potential to introduce significant complexity,
the following sections examine the key issues in more detail, specifically with respect to the
ISO 17024 standard which was raised as a possible standard for the program accreditation
approach.
5.4.5.1. Mutual recognition requirements
Arts
One suggestion was that the US Free Trade Agreement (FTA) should be considered for its
impact on any Australian scheme. Standards Australia similarly noted the importance of
the
ensuring that any Australian scheme does not introduce any restraints to trade.
The Department of Education, Science & Training (DEST) advised that there is a key principle
of mutual recognition embedded in the US FTA and other World Trade Organisation (WTO)
and
relationships. DEST suggested close analysis of any requirement that would make it harder
Infrastructure,
for overseas professionals to practise in Australia. Any such requirement would need to be
clearly justified on the basis of safety, quality or efficacy.
of Sport
The use of international standards such as ISO/IEC 17024 is seen as a useful mechanism for
ensuring this international consistency and providing both for Australian professionals to work
internationally and for overseas professionals to support Australia’s information security
needs.
5.4.5.2. Ensuring certification quality
Department
During the initial interview phase, the importance of ensuring the experience and relevance of
teachers in this field was raised as well as the qualifications, knowledge and experience of
the
teachers and trainers in the information security field.
by Communications,
There were differing views on whether industry or academia made for better teachers. One
view was that as most tertiary education departments require a doctorate in a relevant
discipline before being allowed to teach, educational qualification requirements in academia
1982
are therefore higher than in industry.
There is a belief that current certifications have too much reliance on questions and answers,
Act
and there would be benefits in additional face-to-face assessments by a panel for industry
certifications. This would assess the ability for individuals to think on their feet and ability to
communicate.
FOI Development,
ACS, (ISC)2, ISACA and ISSPCS all acknowledge the relevance and requirement of achieving
accreditation to ISO/IEC 17024-2004:
Conformity assessment – General requirements for
the
bodies operating certification of persons.
ISACA noted that any program accreditation scheme needed a mechanism for recourse, a
Regional
transparent assessment process and consistently high standards. It was acknowledged by all
under
participants that the international standard and relevance of any program put in place would
be paramount.
AITSF noted that while ISO/IEC 17024 would provide a genuine measure of the integrity of
the certification process, it was important to consider other implications:
Achieving compliance to the standard, and being accredited against it, can
Released Transport,
introduce significant cost that is then passed on the consumer/employer; and
Page 46 of 98
IT Security Skills Accreditation in Australia
Accreditation verifies the integrity/suitability of the certification process, not the
content.
At the workshop the point was raised that the point that Australia has two organisations
already accredited to ISO/IEC 17024, in fields unrelated to information security and the
mechanisms for developing such a scheme for information security are already in place
should industry wish to formalise such a scheme at a point in the future.
Arts
5.4.5.3. Recognition of prior learning (RPL) and prior experience (RPE)
the
Organisations differed in their views on the value and importance of including experience as a
requirement of a certification program. This topic was not discussed at the workshop due to
time constraints and as it was not raised as a key issue.
and
It was proposed that any new Australian certification or accreditation program would require a
Infrastructure,
‘grandfathering’ scheme and an acceptance of recognition of prior learning and recognition of
of
prior experience processes. Such a requirement would introduce the need for a governing
Sport
board or panel which would be responsible for conducting assessments. Peer verification of
experience was noted as being important.
Significant pitfalls to be avoided included the tendency to ‘grandfather’ applicants who had not
proven their skills and too much weight being given to experiences that did not validate the
individual’s capability to complete a given job.
(ISC)2 and ISACA also noted that in determining competence, experience was required
Department
beyond security skills, including general management, budgeting, people skills, presentation
skills, and other areas. These areas were best validated through existing human resources
the
and recruitment processes.
by Communications,
It was suggested that an equivalence process of current international certifications should be
made available to Australian citizens, certifying an Australian knowledge base. Migrant
professionals should go through a skilled process to attain this Australian-specific knowledge.
1982
As the focus of discussions for this project was on information security skills certification
programs available in Australia, and this issue was not raised by any other project
participants, the issue of recognising national programs originating outside Australia was not
Act
examined further.
At this stage, industry is supportive of the use of the ISO/IEC 17024 standard to provide for a
FOI Development,
consistent level of process maturity and integrity in the information security skills accreditation
field. However, participants did not see a need for there to be a requirement for a formalised
the
“scheme”, nor for the use of a governing body to oversee such a process. Discussion around
the need for a governing body is dealt with in more detail in section 5.4.7.
under Regional
5.4.6. Awareness Program
Following the workshop meetings further discussions were held with stakeholders on the
broad issue of raising market awareness of information security skills accreditation. Three key
areas or elements of an awareness program to support both small and large enterprises were
identified:
Released Transport,
Awareness of the qualifications available and their relevance/content;
Page 47 of 98
IT Security Skills Accreditation in Australia
Support in defining the requirements for an information security role or project;
and
Support in determining the appropriate checks to be conducted in performing due
diligence on a potential employee or contractor/consultant.
All certification bodies and professional associations agreed that there is a need for better
awareness in the market of the meaning of the currently available certification programs. The
Arts
need for more advertising, awareness and developing brand awareness of information
security professional qualifications was highlighted
the
A number of organisations including ISIG and (ISC)2 noted a requirement for information
security roles to be better defined to allow for more accurately assessing a candidate’s fit to
the position. However, it was noted that while there may be poor definition of such roles, this
and
was no different to many other professional services fields, such as management consulting.
Infrastructure,
It was suggested that a simple mapping between vendor certifications and related product and
product areas would be of value to the market. This could be extended to be a ‘ready
of Sport
reckoner’ to identify job functions by certification to help owners and operators of critical
infrastructure identify the right professionals easily and quickly in order to protect their
systems.
In addition, a ‘Buyer’s Guide’ to IT security professional services would provide a matrix of
disciplines to certification/knowledge areas.
There was also general consensus that employers should understand their own requirements
Department
to conduct due diligence on any proposed employee, regardless of their certification and
experience. It was suggested that a statement/recommendation should be issued to critical
the
infrastructure owners and operators on how to select people in this field. Support to be
Communications,
provided to employers in this area could include providing guidance on the range of
by
background checking mechanisms available, how these are used, and the degree of
assurance provided by each.
Workshop participants emphasised the need to lift the level of awareness so
1982
consumer/employers and professionals both have a better understanding of the complexity of
certification and recruitment within the information security industry. There was also a
Act
requirement for professional organisations to leverage the power of any awareness program
and distribute the knowledge to the consumers/employers of information security services.
FOI Development,
5.4.6 Governing Body
the
During the initial interview phase, participants were asked how an information security skills
accreditation scheme for Australia should be structured. Participants had varying views and
different types of governance were proposed by participants
under Regional
At the workshop however, participants reached a consensus that an information security skills
accreditation scheme was not deemed as an appropriate solution to the issues raised.
Therefore the topic of a governing body was only briefly touched on, and participants
indicated a reluctance to support it.
Released Transport,
Page 48 of 98
IT Security Skills Accreditation in Australia
5.5 DEMAND AND SUPPLY DRIVERS
5.5.1 Driving Acceptance
It was important to ensure current industry practitioners, both with and without certifications,
were in a position to work with any scheme developed. It was clearly indicated by
representatives of information security practitioners that personnel with current international
Arts
certifications are unlikely to pursue an additional certification.
It was noted that Australia needs to attract overseas talent and forcing them to locally certify in
the
addition to international certifications may prove to be a deterrent. A similar challenge is that
of gaining critical mass for an Australian certification when competing against international
and
certifications with a significant head-start.
Infrastructure,
5.5.2
Cost
of Sport
Participants indicated that the cost of any new accreditation process needed to be at a level
that would not increase the cost of information security professional services across the
market.
Specific cost issues were not investigated but it was noted that ensuring no undue financial
burden was placed on information security professionals, or the organisations using their
services, was one of the generally accepted principles.
Department
5.5.3 Structural change
the
It was frequently noted that the information security professional services market in Australia
Communications,
is fragmented and as such contains many individuals operating as either sole traders or in
by
loose affiliations with others. It was suggested by some interviewees that this structural
component of the industry could either be intentionally modified to provide greater control or
could unintentionally be modified through the implementation of an accreditation scheme.
1982
While this is not currently proposed as a specific option, it is however included for
completeness and to remain cognisant of potential flow-on effects.
Act
FOI Development,
the
under Regional
Released Transport,
Page 49 of 98
IT Security Skills Accreditation in Australia
6 CONSENSUS
Following from the workshop, further consultations with key industry groups and certification
bodies were held to provide greater clarity around the specific ‘solutions’ being put forward.
Two specific items receiving the greatest support were:
Arts
An Awareness Program on existing certifications
the
An Australian Training Component for existing certifications
These two items are discussed in greater detail in the following sections.
and
Infrastructure,
6.1 CONSENSUS TOWARD AN INDUSTRY AWARENESS PROGRAM
of Sport
Discussions following from the workshop took place to construct an overview of what an
Awareness Program should encompass, in order to determine how organisations,
professionals and consumer/employers could gain the greatest benefit from its development.
6.1.1
Objectives of an Industry Awareness Program
Participants were asked to highlight objectives an Awareness Program should seek to achieve
Department
in order for it to be relevant to the information security industry as a whole.
1. The Awareness Program should provide a validation of certification quality along with
the
detail on certification content in order to assist information security professionals in
Communications,
selecting the appropriate certification for their job role and career.
by
2. The Awareness Program should provide an accepted point of reference with which to
compare and contrast certification schemes currently available.
1982
3. The Awareness Program should increase the confidence level of consumer/employers
in knowing when help is required for information security, and where to find the right
Act
professionals to do the job. Subsequently, the Awareness Program should help
organisations to realise that security is an on-going process which involves selecting the
right professionals from the start.
FOI Development,
4. In order to maintain vendor neutrality, the Awareness Program should not promote
the
specific certification schemes. The Awareness Program should serve the role of
informing consumer/employers and professionals to allow them to decide on the most
appropriate program for their needs.
Regional
5. The Awareness Program should include sources of knowledge which may not be
under
referenced by current certifications, such as new and accepted references to best
practice.
6.1.2 Delivery Medium
A number of organisations in the initial interview phase proposed the concept of a Buyer’s
Released Transport,
Guide as the medium for disseminating the required information to professionals and
Page 50 of 98
IT Security Skills Accreditation in Australia
consumer/employers. Participants agreed that the Buyer’s Guide should contain information
covering the following:
6.1.2.1 IT Security vs. Information Security
The Buyer’s Guide must differentiate and explain the differences between IT security and
information security to consumer/employers and professionals, to support the correct
definition of the required skill set for a given role.
Arts
6.1.2.2 Roles and Responsibilities
the
The Buyer’s Guide must clearly define job roles and responsibilities within the information
security industry to provide a common guideline for information security professionals
and
practising in Australia. A framework of generally accepted knowledge and skills for specific
information security roles, particularly information security managers, should be included in
Infrastructure,
the Buyer’s Guide.
of Sport
ISSA is currently undertaking an identification mapping process for roles and responsibilities
within the information security industry and is willing to contribute its knowledge in the area to
this effort. ISACA and (ISC)2 have both independently been involved in developing a career
road map for information security professionals. (ISC)2 is still involved in similar efforts
around the world and is willing to share lessons learnt from the exercise. ISACA, however,
has stated that their initiative in the past has had limited success due to the issue of
identification and ‘naming’ of roles within the information security industry globally. ISACA are
Department
currently developing a functional job specification for “Information Security Manager”.
Comments made in regard to positional titles are related not to tasks performed, but labels
the
that are given to those that undertake the tasks in different global locations. As job titles are
generally company specific, (ISC)2 has recommended that the exercise include a task set for
by Communications,
each job role to avoid any confusion or misrepresentation.
6.1.2.3 Qualifications Guideline
1982
The Buyer’s Guide should outline the current qualifications available to information security
professionals and identify areas of similarity and difference between them. The list of
Act
qualifications should include information security programs offered by certification bodies,
various educational institutions and universities. Content should be easily comprehensible and
should summarise the skills and knowledge examined as well as the requirement for
FOI Development,
continuing professional education by each qualification to provide a guideline for
consumer/employers and professionals.
the
6.1.2.4 ISO/IEC 17024 Accredited Certificates
The Buyer’s Guide should inform consumer/employers and professionals on ISO/IEC
17024
under Regional
and its role in providing a quality assurance benchmark for certification bodies. The Buyer’s
Guide should outline the scope of ISO/IEC
17024 and provide information on the criteria for
certification bodies in the development and maintenance of certification schemes. The Buyer’s
Guide should include a list of ISO/IEC
17024 accredited certification schemes.
6.1.2.5 Qualifications Mapping
Released Transport,
Qualifications mapping was the most requested component by industry professionals and
consumer/employers of a proposed Buyer’s Guide. The qualifications mapping should indicate
Page 51 of 98
IT Security Skills Accreditation in Australia
the technical abilities and management skills covered by qualifications. It should also match
certifications to specific job roles.
The purpose of the qualifications mapping would be two-fold. Firstly, consumer/employers will
be better informed on skills and qualification requirements when recruiting for an IT security
role. Secondly, information security professionals will have a relevant reference for choosing
and comparing qualifications for their own professional education and development. The
qualifications mapping would be a critical component of the Buyer’s Guide as it would
Arts
demonstrate that various certifications address different skill and role requirements. In order to
maintain vendor neutrality, it was agreed by industry groups that the qualification mapping of
the
available certifications against recognised information security skills should be completed by
external parties as opposed to certification bodies.
and
6.1.2.6 Directory of Contacts
Infrastructure,
The Buyer’s Guide should include a directory listing of contacts for the certification schemes
of
currently available. The directory should maintain the latest information available for the
Sport
definitive contacts of certification bodies and include details such as head office location,
website address, phone and fax numbers.
6.1.2.7 Due Diligence
The degree to which guidance on due diligence should be included in the Buyer’s Guide was
not agreed across all participants.
Department
While educating the market on available services and approaches for conducting due
diligence was considered a worthwhile endeavour, it was felt that this should not be a core
the
component of the information security skills accreditation awareness program.
by Communications,
6.1.2.8 Suggested Content
While the majority of content areas were agreed at a high level, such as details on the
available certifications, the inclusion of information on ISO 17024, and the appropriateness of
1982
each certification for given job roles and careers, other areas of content was suggested as
adding value to the guide.
Act
It was suggested that the Awareness Program include
FOI Development,
an explanation on Control Objectives for Information and Related Technology
(COBIT),
the
the Information Technology Infrastructure Library (ITIL) in relation to certifications,
basic information on issues such as privacy,
the Sarbanes-Oxley Act and its impact on Australia, and
under Regional
other governance and compliance drivers,
the relevance of certifications being governed by a Code of Ethics and standards.
It is agreed that all the above items would provide valuable information to both
consumer/employers of information security services and information security professionals
themselves. However, it was also acknowledged that it is important to ensure the Buyer’s
Guide does not attempt to solve all information issues in the industry at once. Inclusion of
Released Transport,
Page 52 of 98
IT Security Skills Accreditation in Australia
information outside of the core functions of the Buyer’s Guide should be discussed by the
participants and topics included sparingly.
6.1.3 Participation
For this phase of the project, the following organisations were selected for further
consultations:
Arts
AITSF
the
AusCERT/ISSPCS
(ISC)2
ISACA
and
ISIG
Infrastructure,
ISSA
of
Sport
QUT
SANS.
Resources and other competing priorities permitting, all of the participants interviewed were
keen to contribute industry experience and knowledge towards developing and administrating
the Awareness Program. However, participants also identified the need to negotiate the level
of involvement expected from each stakeholder in the Awareness Program. Details such as
funding, resourcing and timeframes would need to be considered between all organisations
Department
involved in the Awareness Program. Organisations were also willing to promote the
Awareness Program provided the content was appropriate.
the
by Communications,
6.2 CONSENSUS TOWARDS A TRAINING COMPONENT
In conjunction with the Awareness Program, an Australian training component was proposed
1982
as a solution to address the lack of regional knowledge faced by professionals who practise in
the Australian information security environment. After the workshop, key industry group
members and certification body representatives were consulted to construct an overview of
Act
what the Australian training component should encompass in order to meet the needs of
industry.
FOI Development,
6.2.1
Objectives
the
Participants were asked to identify objectives the Australian training component should seek
to achieve in order for it to be valuable and useful to information security professionals.
Regional
1. The Australian training component should address the lack of knowledge in the area of
under
legal and regulatory matters in the Australian work environment. However, it was
observed by all participants that the Australian training component should be developed
with the understanding that information security professionals should not be experts on
legal and regulatory matters.
2. The Australian training component should validate that the legal information and advice
Released Transport,
provided to information security professionals by lawyers is appropriate.
Page 53 of 98
IT Security Skills Accreditation in Australia
3. The Australian training component should be an optional choice for information security
professionals in Australia and it should be economically priced.
6.2.2 Content
Participants were asked to identify topics which are specific to Australia and require better
coverage in order for information security professionals to have a better understanding of the
Arts
domestic information security environment.
6.2.2.1 Legal and Regulatory
the
The Australian training component should cover the essential knowledge of practising
information security within the context of Australian regulations and legislation such as the
and
Privacy Act 1988. Professionals undergoing the Australian training component should gain an
Infrastructure,
understanding of the requirements of local legislation and regulation. It was that while
information security professionals would then be familiar with the Australian legal and
of Sport
regulatory framework they would remain unable to offer professional legal advice in this field.
Industry groups have suggested that the Australian training component should also outline the
relevance of international legislation, such as the Sarbanes-Oxley Act 2002, in the Australian
information security environment.
6.2.2.2 Code of Ethics
Department
As part of the Australian training component, SANS has recommended Australia set a
precedent by presenting a standard Code of Ethics for information security professionals
which can be practised globally. However, it has been observed by ISACA that most
the
certification bodies already have their own Code of Ethics by which certified professionals are
by Communications,
obliged to abide. (ISC)2 observed that the ethics requirements are unlikely to vary from
country to country and ethical practices in Australia would not be different from internationally
accepted practices.
1982
6.2.2.3 Social and Cultural
Participants were asked if topics like Australian social and cultural issues should be
Act
addressed by the Australian training component. Participants from industry groups decided
against including social and cultural issues, and certification bodies offered support only if the
FOI Development,
inclusion of social and cultural issues were deemed necessary by industry.
the
6.2.2.4 Australian Standards and Guidelines
SANS has suggested that it would be appropriate for the Australian training component to
explain the relevance of Australian security guidelines such as the Australian Government
Regional
Information and Communications Technology Security Manual (ACSI 33). Another standard
under
put forward for inclusion in the Australian training component is the Australian Government’s
Protective Security Manual (PSM) however it is noted that this standard is not publicly
available.
Released Transport,
Page 54 of 98
IT Security Skills Accreditation in Australia
6.2.2
Participation
For this phase of the project, the following organisations were selected for further
consultations:
AITSF
AusCERT/ISSPCS
Arts
(ISC)2
ISACA
the
ISIG
ISSA
and
QUT
SANS.
Infrastructure,
However, not all organisations agreed to be involved with the development and administration
of Sport
of the Australian training component.
AITSF has declined to be involved as a major stakeholder in the Australian training
component initiative as it believes that an international perspective is more crucial to an
effective program than is an Australian training component.
Organisations which did agree to be involved with the Australian training program again
asserted the need to negotiate the level of involvement for each stakeholder. For the
Department
certification bodies, it was important to distinguish ownership of material contributed to the
Australian training component and ensure accuracy of the localised content.
the
6.2.3 Competition
by Communications,
A potential model discussed for the Australian training component was for the component to
be collaboratively developed by interested stakeholders, and to be incorporated – formally or
informally – into existing certification and qualification schemes. The inclusion of the
1982
Australian component in the examination/certification stage was not assumed, however
through the inclusion of this material in the supporting training programs, an opportunity will
Act
exist for Australian information security professionals to be exposed to this information.
It is not proposed that the Australian training component would compete with existing
FOI Development,
certifications rather it would be an additional body of knowledge offered by existing
certification providers. Certification bodies were asked at interview if they would be willing to
the
support such a component.
SANS has agreed in principle not to compete with the Australian training component and will
promote such a program to information security professionals on the condition that the
Regional
material presented in the program is of high quality.
under
Although ISACA does not view competition as an issue, it has reserved final judgment until
the content and context of the Australian training component are known. ISACA has
requested clarity and definition on the purpose and intention of the Australian training
component as well as areas of the material that may be covered by existing programs.
It was observed that ensuring the content taught in the Australian training component does
Released Transport,
not conflict with current certification material will be difficult to achieve if a consensus is not
Page 55 of 98
IT Security Skills Accreditation in Australia
reached by industry and certification organisations. While consensus is not impossible to
achieve, it may become a barrier to the progress of the Australian training component.
Furthermore, as certification schemes evolve and improve, there could be overlap between
topics covered by the Australian training component and certification schemes.
(ISC)2 believes it is not in the interests of the information security community to have
duplication of effort and says the Australian training component should not compete with
existing training, education and certification products. (ISC)2 observed that it would be difficult
Arts
to exclude itself from providing educational products that could help in the development of its
Australian constituents. The exact nature of the Australian training program and how it fits with
the
the (ISC)2 charter will dictate the level of (ISC)2 participation.
and
Infrastructure,
of Sport
Department
the
by Communications,
1982
Act
FOI Development,
the
under Regional
Released Transport,
Page 56 of 98
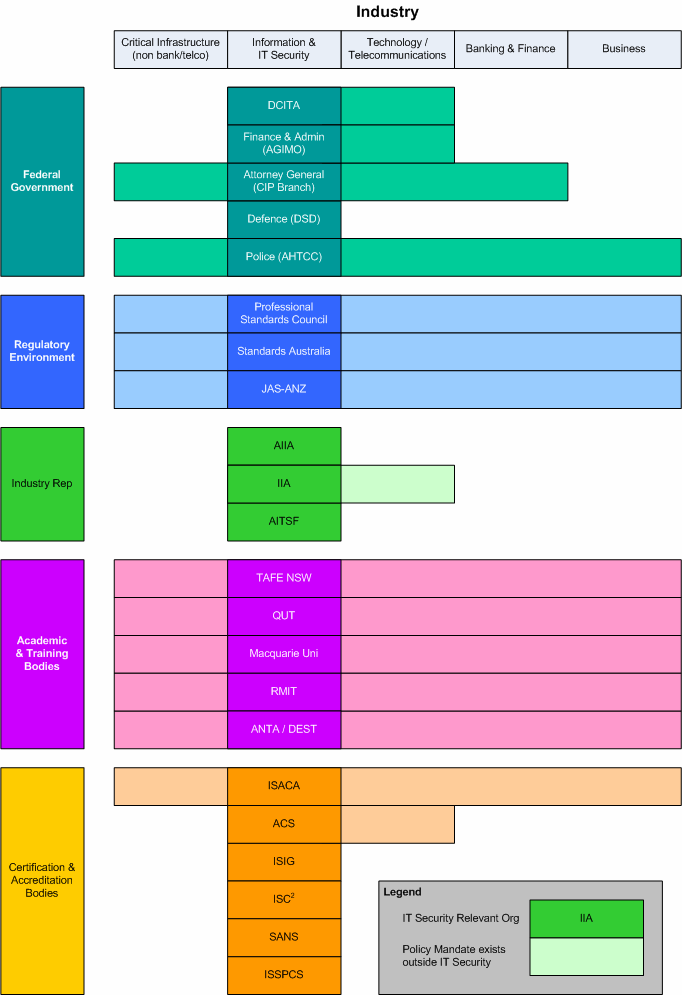
IT Security Skills Accreditation in Australia
8
APPENDIX B - SUMMARY OF PARTICIPATING ORGANISATIONS
The following diagram illustrates the spectrum of industries and industry sectors involved in
this project.
Arts
the
and
Infrastructure,
of Sport
Department
the
by Communications,
1982
Act
FOI Development,
the
under Regional
Released Transport,
Page 63 of 98
IT Security Skills Accreditation in Australia
Figure 3: Spectrum of industries and sector areas
AGIMO – Australian Government Information Management Office
The Australian Government Information Management Office (AGIMO), Department of Finance
and Administration is working towards making Australia a leader in the productive application
of information and communications technologies to government administration, information
Arts
and services. AGIMO provides strategic advice, activities and representation relating to the
application of ICT to government administration, information and services.
the
URL: http://www.agimo.gov.au/about
and
AGL – Australian Gas Light Company
Infrastructure,
AGL has been a major participant in the Australian energy industry since 1837. Today AGL is
of
a major retailer of gas and electricity to about three million customers. AGL also has an
Sport
extensive portfolio of wholly and partly-owned investments in energy infrastructure,
infrastructure management and other energy companies.
URL: http://www.agl.com.au/AGLNew/default.htm
AHTCC – Australian High Tech Crime Centre
Department
The Australian High Tech Crime Centre’s (AHTCC) purpose is to enforce Australian law in
combating serious crime involving complex technology. AHTCC is hosted by the Australian
the
Federal Police (AFP) in Canberra and includes representation from all Australian State and
Communications,
Territory police forces, both in its staff and Board of Management.
by
The role of the AHTCC is to:
Provide a national coordinated approach to combating serious, complex and multi-
1982
jurisdictional high tech crimes, especially those beyond the capability of single
jurisdictions;
Act
Assist in improving the capacity of all jurisdictions to deal with high tech crime; and
Support efforts to protect the National Information Infrastructure.
FOI Development,
URL: http://www.ahtcc.gov.au/
the
AIIA – Australian Information Industry Association
AIIA is a representative body in Australia for the Information and Communications Technology
Regional
(ICT) industry. AIIA works across many areas to assist the ICT industry to meet its business
under
objectives in corporate and government markets.
URL: http://www.aiia.com.au/i-cms.isp
AOEMA – Asia Oceanic Electronic Marketplace Association
Released Transport,
The Asia Oceanic Electronic Marketplace Association (AOEMA) is a not-for-profit organisation
which develops the use of secure global electronic commerce. AOEMA has been working with
Page 64 of 98
IT Security Skills Accreditation in Australia
the APEC Telecommunications and Information Working Group since its inception and
provides services to assist small and micro enterprises in all countries in the region.
URL: http://www.aoema.org
AGD CIP – Attorney-General’s Department Critical Infrastructure Protection Branch
The Critical Infrastructure Protection Branch of the Attorney-General's Department is
responsible for the development and coordination of Australian Government policy and
international cooperation relating to critical infrastructure protection, including the National
Information Infrastructure (NII). The branch also provides general and legal policy advice and
coordination within the department on e-security (including its relationship to high-tech crime),
and cyber-terrorism.
URL: http://www.ag.gov.au/agd/WWW/securitylawHome.nsf/Page/Critical Infrastructure
Sport and the Arts
AusCERT – Australian Computer Emergency Response Team
AusCERT is the national Computer Emergency Response Team for Australia. As a trusted
Australian contact within a worldwide network of computer security experts, AusCERT
provides computer incident prevention, response and mitigation strategies for members, a
national alerting service and an incident reporting scheme.
URL: http://www.auscert.org.au/
ACS – Australian Computer Society
Communications,
The Australian Computer Society (ACS) is a representative association for Information &
Communications Technology (ICT) professionals in Australia. The society has a large and
active membership from all levels of the ICT industry. A member of the Australian Council of
Professions, the ACS is a public voice of the ICT profession and an advocate of professional
ethics and standards in the ICT industry, with a commitment to the wider community to ensure
Act 1982 by the Department of Infrastructure,
the beneficial use of ICT.
URL: http://acs.org.au/
Development,
AITSF- Australian IT Security Forum
The mission of the Australian IT Security Forum is to promote information security within the
Australian information economy, through the development of associated technologies,
capabilities and services, and to advance the Australian information security industry
under the FOI
internationally.
URL: http://www.aitsf.aeema.asn.au/
Released Transport, Regional
Page 65 of 98
IT Security Skills Accreditation in Australia
Bridge Point Communications
Bridge Point is a provider of both Information security consulting, training and network
integration services. Since commencing operations in Brisbane, Australia in 2000, Bridge
Point has developed a team of experienced consultants and engineers who have successfully
completed a wide range of information security and networking projects.
URL: http://www.bridgepoint.com.au
Arts
Centrelink
the
Centrelink is a government agency delivering a range of Commonwealth services to the
Australian community. Centrelink’s inception was motivated by the amalgamation of
and
community service agencies to provide a central point of contact.
Infrastructure,
URL: http://www.centrelink.gov.au
of Sport
CBA – Commonwealth Bank of Australia
The Commonwealth Bank of Australia (CBA) is one of Australia’s largest financial institutions
with businesses in New Zealand, Asia and the United Kingdom. CBA provides banking and
financial services for all Australians.
URL: http://www.commbank.com.au/default.asp
Department
the
DSD – Defence Signals Directorate
Communications,
The Defence Signals Directorate’s purpose is to support the Australian Government decision-
by
makers and the Australian Defence Force with high-quality foreign signals intelligence
products and services. The DSD ensures certainty and effectiveness in Government and
Defence policies by providing important information that is not available from open sources to
1982
policy departments and assessment agencies. The DSD also provides a range of information
security services to the Australian Defence Force and Australian Government agencies to
Act
ensure that their electronic information systems are not susceptible to unauthorised access,
compromise or disruption.
FOI Development,
URL: http://www.dsd.gov.au
the
eSecurity Australia
eSecurity Australia is an unincorporated cluster of approximately 35 e-security related
Regional
organisations. The group was formed in early 2001 in Queensland, Australia.
under
URL: http://www.esecurityaustralia.com/
Hutchison Telecommunications
Released Transport,
Page 66 of 98
IT Security Skills Accreditation in Australia
Hutchison Telecommunications (Australia) Limited is a mobile communications company,
offering Australian mobile consumers a choice of services from two distinct global brands,
Orange and 3.
URL: http://www.hutchison.com.au
IIA – Internet Industry Association
Arts
The Internet Industry Association is Australia's national internet industry organisation.
Members include telecommunications carriers, content creators and publishers, web
the
developers, e-commerce traders and solutions providers, hardware vendors, systems
integrators, banks, insurance underwriters, technology law firms, ISPs, educational
and
institutions, research analysts, and those providing professional and technical support
services.
Infrastructure,
URL: http://www.iia.net.au
of Sport
ING Australia
ING is one of Australia's leading fund managers and life insurers with more than $38 billion in
assets under management. ING Australia was founded in Sydney in 1878 as Mercantile
Mutual. In 1982 it became part of what is now ING Group. ING provides a range of financial
products and services through a network of advisers and financial institutions.
Department
URL: http://www.ing.com.au
the
by Communications,
ISACA – Information Systems Audit and Control Association
With more than 47,000 members in more than 140 countries, the Information Systems Audit
and Control Association (ISACA) is a well-recognised IT governance, control, security and
1982
assurance organisation. ISACA develops international information systems auditing and
control standards and administers the globally respected CISA and CISM certifications.
Act
URL: http://www.isaca.org
FOI Development,
(ISC)2 – International Information Systems Security Certification Consortium
the
The International Information Systems Security Certification Consortium (ISC)2², is a non-
profit organisation. (ISC)2’s main functions are:
Maintaining the CBK for information security;
under Regional
Certifying industry professionals and practitioners under an international standard,
Providing education;
Administering certification examinations; and
Ensuring the continued competence of credential holders.
URL: https://www.isc2.org
Released Transport,
Page 67 of 98
IT Security Skills Accreditation in Australia
ISIG – Information Security Interest Group
The Information Security Interest Group (ISIG) branches exist in Sydney, Melbourne,
Canberra, Brisbane and Adelaide. ISIG currently has more than 200 paid members and more
than 500 ‘friends’ on its mailing list. ISIG is an organisation for individuals rather than
companies. Membership ranges from company CEOs through to highly skilled technical
security specialists.
URL:
Arts
http://www.isig.org.au
the
ISSA – Information Systems Security Association
and
The Information Systems Security Association (ISSA) is a not-for-profit international
Infrastructure,
organisation of information security professionals and practitioners. ISSA provides educational
forums, publications and peer interaction opportunities that enhance the knowledge, skill and
of Sport
professional growth of its members.
URL: http://www.issa.org
ISSPCS Academic Board
ISSPCS Academic Board’s purpose is to ensure the ISSPCS certifications stay relevant and
Department
focused on current and realistic commercial, governmental and academic interests. The board
controls the curricular and assessment aspects of the certification.
the
URL: http://www.isspcs.org/board/
by Communications,
JAS-ANZ – Joint Accreditation System of Australia & New Zealand
JAS-ANZ is a not-for-profit, self-funding international organisation established under a treaty
1982
between the Governments of Australia and New Zealand to act as the joint accreditation body
for Australia and New Zealand for certification of management systems, products and
Act
personnel.
URL: http://www.jas-anz.com.au/showpage.php
FOI Development,
the
Macquarie University
Macquarie University, situated in Sydney's north-west, has a reputation as an innovator in
higher education learning and research. Macquarie has developed and enhanced a high-
Regional
performance research culture in key areas of environmental science, social sciences,
under
commerce, the humanities (including the Macquarie Dictionary Centre) plus science and
technology.
URL: http://www.mq.edu.au/
Released Transport,
Microsoft
Page 68 of 98
IT Security Skills Accreditation in Australia
Microsoft was founded in 1975, with the local Australian operation starting in 1983. An
estimated 16 million Australians use Microsoft products from home to the office. Microsoft has
a staff of more than 700 people working across Australia, as well as ninemsn, and Microsoft’s
Home and Entertainment Division.
URL: http://www.microsoft.com/australia
Arts
the
and
Infrastructure,
of Sport
Department
the
by Communications,
1982
Act
FOI Development,
the
under Regional
Released Transport,
Page 69 of 98
IT Security Skills Accreditation in Australia
PSC – Professional Standards Council
The Professional Standards Council was established in 1995 under the Professional
Standards Act 1994 (NSW) and also later under the Professional Standards Act 1997 (WA).
Under the Act, the council’s role is to advise, monitor, educate and advocate on issues
affecting occupational associations, professionals and consumers in general. PCS’s 11
council members come from a variety of professions and disciplines. They are appointed by
the Attorney-General.
Arts
URL: http://www.agd.nsw.gov.au/psc
the
QUT – Queensland University of Technology
and
Queensland University of Technology (QUT) is one of Australia's largest universities, enrolling
Infrastructure,
40,000 students, 12 per cent from overseas. QUT offers a range of undergraduate degrees,
with the flexibility to choose a combination of study areas as well as participate in exchange
of Sport
programs with overseas universities.
URL: http://www.qut.edu.au
RMIT University – Royal Melbourne Institute of Technology
RMIT offers more than 200 TAFE and higher educational programs across a broad range of
Department
fields. Traditional strengths such as engineering, business and IT sit beside popular
contemporary fields including life sciences, communications and fashion.
the
URL: http://www.rmit.edu.au
by Communications,
SAI Global
SAI Global Limited is a business publishing, training and assurance organisation with offices
1982
in Australia, New Zealand, United States and across Asia. SAI Global delivers an integrated
range of standards and business improvement-related products and services ranging from
Act
occupational health and safety systems to risk and environmental management training.
URL: http://www.saiglobal.com.au/
FOI Development,
the
SANS Institute
SANS is a provider of information security training and certification around the world. It also
develops, maintains, and makes available at no cost, a large collection of research documents
Regional
about various aspects of information security, and it operates the internet's early warning
under
system -– Internet Storm Center. Its programs now reach more than 165,000 security
professionals, auditors, system administrators, network administrators, chief information
security officers, and CIOs.
URL: http://www.sans.org
Released Transport,
Page 70 of 98
IT Security Skills Accreditation in Australia
SingTel Optus
SingTel Optus provides a broad range of communications services including mobile, national
and long-distance services, local telephony, international telephony, business network
services, internet and satellite services and subscription television.
URL: http://www.optus.com.au/portal/site/WOCA/
Arts
Standards Australia
the
Standards Australia is a leading standards development organisation in Australia. Standards
Australia strives to enhance Australia’s economic efficiency, international competitiveness and
the community’s expectations for a safe and sustainable environment.
and
URL: http://www.standards.org.au
Infrastructure,
of Sport
TAFE NSW
TAFE New South Wales is Australia's largest educational institution offering more than 1200
courses at more than 130 locations across the state of New South Wales. TAFE NSW
delivers study programs and services to meet the needs of students, industry and the
community.
URL: http://www.tafensw.edu.au
Department
the
Telstra
Communications,
Telstra is a telecommunications and information services company in Australia. Telstra’s main
by
activities include the provision of:
Basic access services to most homes and businesses in Australia;
1982
Local and long-distance telephone calls in Australia and international calls to and
from Australia;
Act
Mobile telecommunications services; a comprehensive range of data and internet
services;
FOI Development,
Management of business customers' IT and/or telecommunications services;
wholesale services to other carriers and carriage service providers;
the
Advertising, directories and information services; and
Cable distribution services for FOXTEL's cable subscription television services.
URL: http://www.telstra.com.au
under Regional
Vodafone
Vodafone provides GSM mobile telecommunications services with network coverage in
Sydney, Melbourne, Canberra, Brisbane, Adelaide and Perth.
URL:
Released Transport,
http://vodafone.com.au
Page 71 of 98
IT Security Skills Accreditation in Australia
9 APPENDIX C: 17799 MAPPING FOR
CISSP, CISA, CISM AND ISSPCS (PRACTITIONER LEVEL)
Introduction
Arts
As discussed within the body of this report, there has been considerable discussion around
the appropriateness of a single “body of knowledge”, and the source of such a body.
the
Based on feedback during the initial interview process, SIFT presented the following as
potential bodies of knowledge to the workshop participants:
and
ISO 17799
Infrastructure,
AS/NZS 7799.2
of
CISSP CBK; and
Sport
NSTISSC 4011.
Discussion led to an understanding that there could be no agreement on a ‘body of
knowledge’ until job skills within information security had been identified.
Similarly, it is acknowledged that to attempt to “map” existing certifications to an information or
IT security standard, implies that there is some attempt on the part of those certifications to
Department
provide full coverage. As the certifications are primarily based on required job skills, there is
no guarantee of a direct mapping to the standards.
the
Within this context, the following four sections provide mappings of CISSP, CISA, CISM and
Communications,
ISSPCS (Practitioner) to the ISO 17799 standard. As is stated within the report, this is
by
intended primarily to be a point of departure for subsequent efforts to increase the awareness
of the programs, and the comparability of the programs.
1982
Act
FOI Development,
the
under Regional
Released Transport,
Page 72 of 98
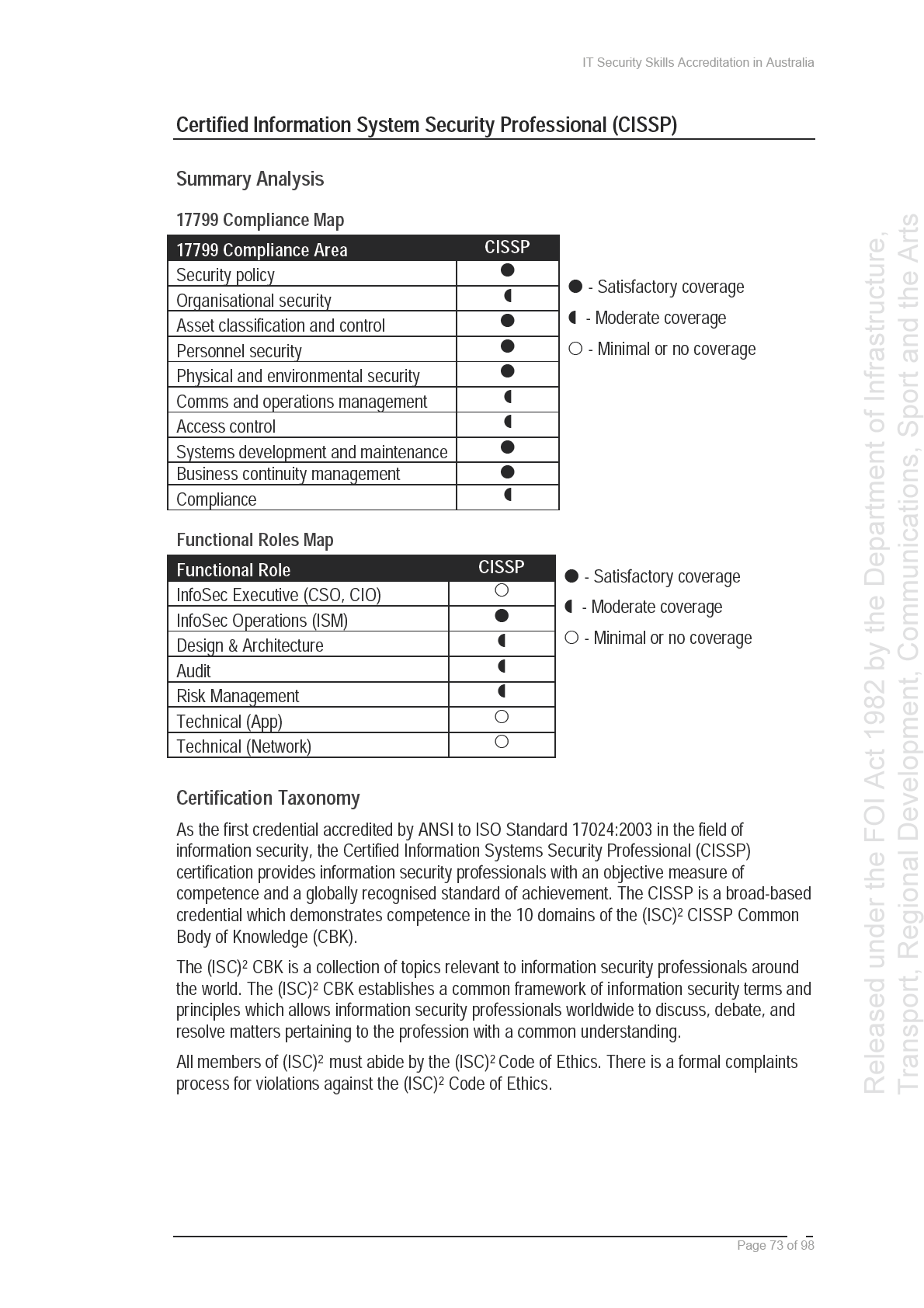
IT Security Skills Accreditation in Australia
Body of Knowledge
Domain 1. Access controls
Domain 2. Telecom & network security
Domain 3. Security management
Domain 4. Applications security
Domain 5. Cryptography
Arts
Domain 6. Security architecture
the
Domain 7. Operations security
Domain 8. Business continuity planning
Domain 9. Law, investigations & ethics
and
Domain 10. Physical security.
Infrastructure,
Issuer
of Sport
The International Information Systems Security Certification Consortium, Inc., or (ISC)2, is a
non-profit organisation, incorporated in the Commonwealth of Massachusetts, based in Palm
Harbour, Florida, USA
Goal(s) of the Certification Body
Department
The (ISC)2 is dedicated to:
Maintaining the CBK for information security;
the
Certifying industry professionals and practitioners under an international standard;
by Communications,
Providing education;
Administering certification examinations; and
Ensuring the continued competence of credential holders.
1982
Business Drivers for Implementing the Certification
Act
People are the key to a secure organisation.
FOI Development,
Technology solutions alone cannot protect an organisation's critical information assets.
Employers demanding qualified information security staff give their organisations a leading
edge by providing the highest standard of security for the information assets of customers,
the
employees, stakeholders and organisations. (ISC)2 is a non-profit body charged with
maintaining, administering and certifying information security professionals via the
compendium of industry best practices and the the (ISC)2 CBK.
under Regional
Benefits of Certification to the Professional
Demonstrates a working knowledge of information security;
Confirms commitment to profession;
Offers a career differentiator, with enhanced credibility and marketability; and
Released Transport,
Provides access to valuable resources, such as peer networking and idea
exchange .
Page 74 of 98
IT Security Skills Accreditation in Australia
Benefits of Certification to the Enterprise
Establishes a standard of best practices;
Offers a solutions-orientation, not specialisation, based on the broader
understanding of the (ISC)2 CBK;
Allows access to a network of global industry and subject matter/domain experts;
Makes broad-based security information resources readily available;
Arts
Adds to credibility with the rigour and regimen of the certification examinations;
and
the
Provides a business and technology orientation to risk management.
and
Target Audience
Infrastructure,
The CISSP credential is ideal for middle and senior level managers who are working toward
or have already attained positions as CISOs, CSOs or Senior Security Engineers.
of Sport
Experience Requirements
Applicants must have a minimum of four years of direct full-time security professional work
experience in one or more of the 10 domains of the (ISC)2 CISSP CBK or three years of direct
full-time security professional work experience in one or more of the 10 domains of the CISSP
CBK with a university degree. Additionally, a Master Degree in Information Security from a
Department
National Centre of Excellence can substitute for one year towards the four-year requirement.
CISSP professional experience includes:
the
Work requiring special education or intellectual attainment, usually including a
by Communications,
liberal education or university degree;
Work requiring habitual memory of a body of knowledge shared with others doing
similar work;
1982
Management of projects and/or other employees;
Supervision of the work of others while working with a minimum of supervision of
Act
one's self;
Work requiring the exercise of judgment, management decision-making, and
Development,
discretion;
FOI
Work requiring the exercise of ethical judgment (as opposed to ethical behaviour).
the
Creative writing and oral communication;
Teaching, instructing, training and the mentoring of others;
Research and development;
under Regional
The specification and selection of controls and mechanisms; ie, identification and
authentication technology (does not include the mere operation of these controls);
and
Applicable titles such as officer, director, manager, leader, supervisor, analyst,
designer, cryptologist, cryptographer, cryptanalyst, architect, engineer, instructor,
professor, investigator, consultant, salesman, representative, etc. Title may
Released Transport,
include programmer. It may include administrator, except where it applies to one
Page 75 of 98
IT Security Skills Accreditation in Australia
who simply operates controls under the authority and supervision of others. Titles
with the words ‘coder’ or ‘operator’ are likely excluded.
Timeliness
The (ISC)2 CBK, from which the (ISC)2 credentials are drawn, is updated annually by the
(ISC)2 CBK Committee to reflect the most current and relevant topics required to practise the
Arts
profession of information security.
the
Distribution & Examination Methods
Preparation method - Review Seminar
and
(ISC)2 offers seminars that help candidates review and refresh their knowledge of information
Infrastructure,
security. The review seminars are classroom-based events held worldwide on a regular basis.
(ISC)
of
2-endorsed seminars are only conducted by instructors authorised by (ISC)2. Instructors
Sport
must be experts in the CISSP CBK domains and remain up to date on the latest information
security-related developments.
This CISSP CBK Review Seminar is the only CBK review seminar endorsed by (ISC) 2..
The (ISC)2 CISSP five-day seminar includes:
Five sessions, each of eight hours duration;
Department
Post-Seminar Self-Assessment;
100 per cent up-to-date material;
the
Contributions from CISSPs, (ISC)2-authorised instructors and subject matter
Communications,
experts; and
by
An overview of the scope of the information security field.
Delivery of Exam
1982
The examination is seated under the supervision of a local third party partner.
Act
Exam Details
250 multiple-choice questions;
FOI Development,
Six hours;
Pass the CISSP exam with a scaled score of 700 points or greater; and
the
Submit a properly completed and executed Endorsement Form.
Identity Verification
under Regional
Identify is verified by local third party partner.
Re-certification requirements
Upon successfully completing the CISSP examination, the student will receive a certificate
and ID card. The student will also be eligible for listing in the CISSP Directory; participation in
Released Transport,
the Speakers' Bureau; serving on (ISC)2 committees and participation in its annual elections.
Page 76 of 98
IT Security Skills Accreditation in Australia
Re-certification is required every three years, with ongoing requirements to maintain their
credentials in good standing. This is primarily accomplished through continuing professional
education (CPE), 120 credits of which are required every three years.
CISSPs must pay an annual maintenance fee of USD$85 per year.
Number of Holders
Arts
As at 1 February 2005:
the
30,681 – Worldwide
503 – Australia
and
Cost
Infrastructure,
Early – USD$499
of Sport
Standard – USD$599
Annual CPE maintenance fees of USD$85.
Completeness
The CISSP Common Body of Knowledge has a satisfactory level of detail but does not have
full coverage of ISO/IEC
17799 topics. ISO/IEC
17799 areas lacking include:
Department
4.2 Security of Third Party Access
8.2 System Planning and Acceptance
the
8.5 Network Management
by Communications,
9.4 Network Access Control
9.5 Operating System Access Control
9.6 Application Access Control
1982
10.4 Security of System Files
12.2 Reviews of Security Policy and Technical Compliance.
Act
Availability
FOI Development,
Registration for the CISSP examination is available worldwide.
the
under Regional
Released Transport,
Page 77 of 98
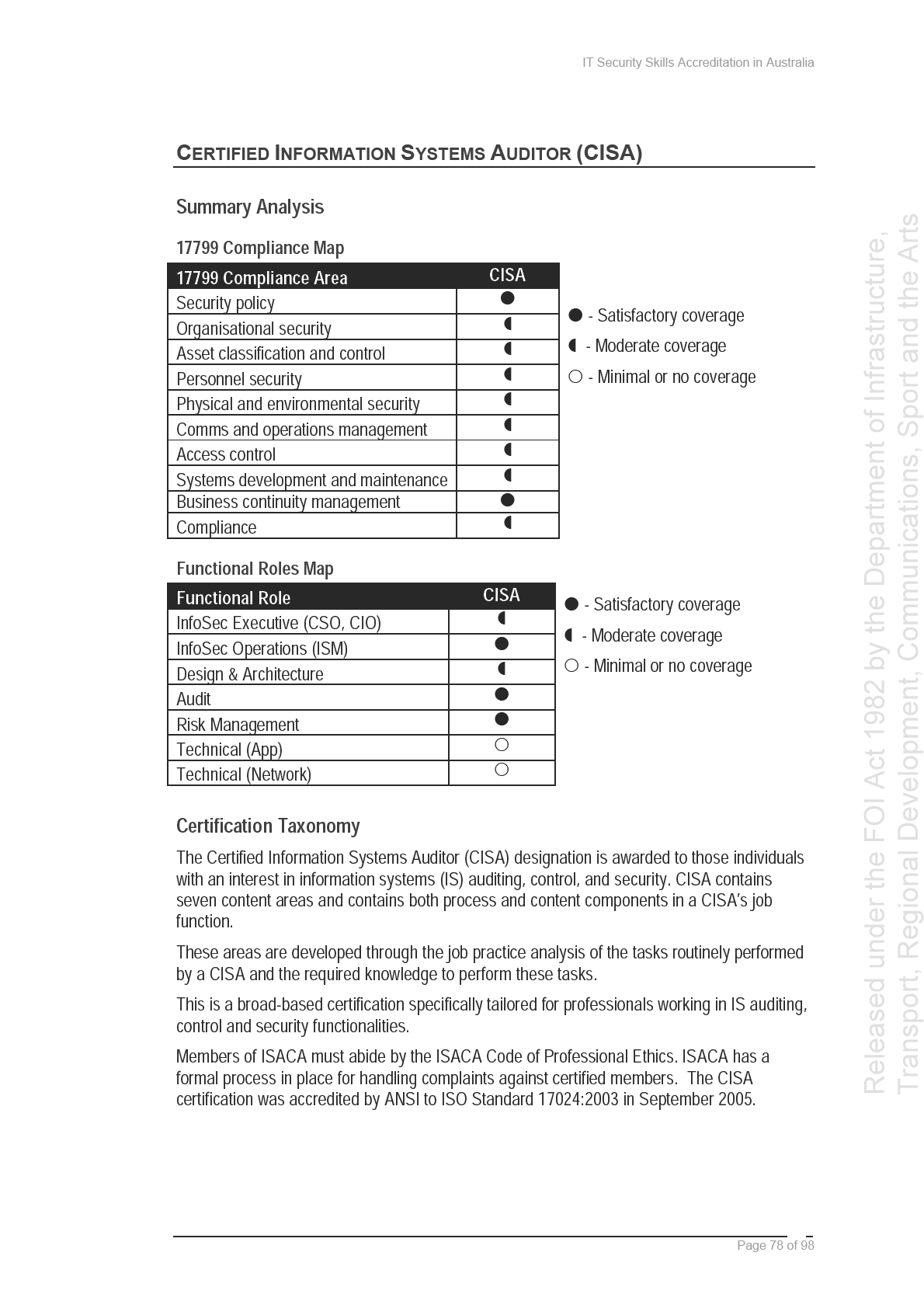
IT Security Skills Accreditation in Australia
CISA Content Areas
Domain 1. Management, Planning, and Organisation of IS
Domain 2. Technical Infrastructure and Operational Practices
Domain 3. Protection of Information Assets
Domain 4. Disaster Recovery and Business Continuity
Domain 5. Business Application System Development, Acquisition,
Arts
Implementation, and Maintenance
Domain 6. Business Process Evaluation and Risk Management
the
Domain 7. The IS Audit Process.
and
Issuer
Infrastructure,
The Information Systems Audit and Control Association (ISACA), Rolling Meadows, Illinois
USA.
of Sport
Goal(s) of the Certification Body
ISACA is dedicated to serving the needs of its members, who are internal and external
auditors, CEOs, CFOs, CIOs, educators, information security and control professionals,
students, and IT consultants.
Department
Business Drivers for Implementing the Certification
the
Since 1978, the CISA program has become a globally accepted standard for IS audit, control
and security professionals.
by Communications,
The technical skills and practices that CISA promotes and evaluates are key functional areas
within the field. With a growing demand for professionals possessing IS audit, control and
security skills, CISA has become a well-regarded certification program by individuals and
1982
organisations around the world. CISA certification signifies commitment to serving an
organisation and the IS audit, control and security industry. In addition, it presents a number
Act
of professional and personal benefits.
Benefits of Certification to the Professional
FOI Development,
Worldwide recognition;
the
Professional development opportunities as a large portion of CISAs hold
management or consulting positions;
Certification equips the professional with the knowledge and ability to evaluate:
Regional
1. IS management strategy, policies, standards and procedures;
under
2. Effectiveness and efficiency of an organisation’s implementation and ongoing
management of technical and operational infrastructure;
3. Logical, environmental and IT infrastructure security;
4. Continuity of business operations and IS processing;
5. Business application system development, acquisition, implementation and
Released Transport,
maintenance;
Page 79 of 98
IT Security Skills Accreditation in Australia
6. Business systems and processes.
Benefits of Certification to the Enterprise
Certification demonstrates IT assurance knowledge and skill;
Certification shows the professional is committed to maintaining skills through
future professional development and continuing professional education; and
Arts
Certifies that the professional has acquired professional experience and has
passed a rigorous exam.
the
Target Audience
and
The CISA certification is designed for professionals who have Information Security Audit,
Control and Security functions as part of their job description.
Infrastructure,
CISA is offered in the following languages: Chinese (Simplified and Traditional), Dutch,
of Sport
English, French, German, Hebrew, Italian, Japanese, Korean and Spanish.
Experience Requirements
A minimum of five years of professional information systems auditing, control or security work
experience (as described in the job content areas) is required for certification. Experience
must have been gained within the 10-year period preceding the application date for
certification or within five years from the date of initially passing the examination. Retaking
Department
and passing the examination will be required if the application for certification is not submitted
within five years from the passing date of the examination. All experience will be verified
the
independently with employers.
by Communications,
Experience substitutions
Substitutions and waivers of such experience may be obtained as follows:
1982
A maximum of one year of information systems experience or one year of financial
or operational auditing experience can be substituted for one year of information
systems auditing, control or security experience;
Act
60 to 120 completed university semester credit hours (the equivalent of an
associate or bachelor degree) can be substituted for one or two years,
FOI Development,
respectively, of information systems auditing, control or security experience; and
Two years as a full-time university instructor in a related field (eg, computer
the
science, accounting, information systems auditing) can be substituted for one year
of information systems auditing, control or security experience.
under Regional
Timeliness
Due to the importance of the job task analysis and the change experienced in the information
security profession, the CISA content material will be subject to change beginning in 2006.
Released Transport,
Page 80 of 98
IT Security Skills Accreditation in Australia
Distribution & Examination Methods
Preparation method - Review Seminar
ISACA offers review seminars prior to the scheduled exam periods. Information regarding
these seminars is available by contacting the local ISACA chapter or checking the website.
(Currently, there are no Australian seminars listed).
Arts
Delivery of Exam
The examination is seated under supervision twice a year in December and June.
the
Exam Details
and
200 multiple-choice questions
Infrastructure,
Four hours
A candidate must score a 75 or higher.
of Sport
Identity Verification
Identify is verified by a Testing Agency Representative.
Re-certification requirements
In order to become and remain a CISA an individual must agree to comply with the CISA
Department
continuing professional education program. This program requires an individual to earn a
minimum of 20 hours annually and 120 hours every three years of continuing professional
the
education.
by Communications,
CISA holders must also pay an annual maintenance fee:
ISACA members: USD $40
ISACA non-members: USD $60.
1982
Number of Holders
Act
As at March 2005:
FOI Development,
Over 38,000 – Worldwide
680 – Oceania.
the
Cost
Early – USD$335 (ISACA members), USD$455 (ISACA non-members)
under Regional
Standard – USD$385 (ISACA members), USD$505 (ISACA non-members)
Annual CPE maintenance fees of USD$40 (ISACA members), USD$60 (ISACA
non-members).
Completeness
Released Transport,
The CISA Domains have a satisfactory level of detail but do not have full coverage of ISO/IEC
17799 topics. ISO/IEC
17799 areas lacking include:
Page 81 of 98
IT Security Skills Accreditation in Australia
5.2 Information Classification
6.1 Security in Job Definition and Resourcing
7.3 General Controls
8.6 Media Handling and Security
9.4 Network Access Control
9.5 Operating System Access Control
Arts
9.8 Mobile Computing and Teleworking.
the
Availability
Registration for the CISA examination is available worldwide.
and
Infrastructure,
of Sport
Department
the
by Communications,
1982
Act
FOI Development,
the
under Regional
Released Transport,
Page 82 of 98
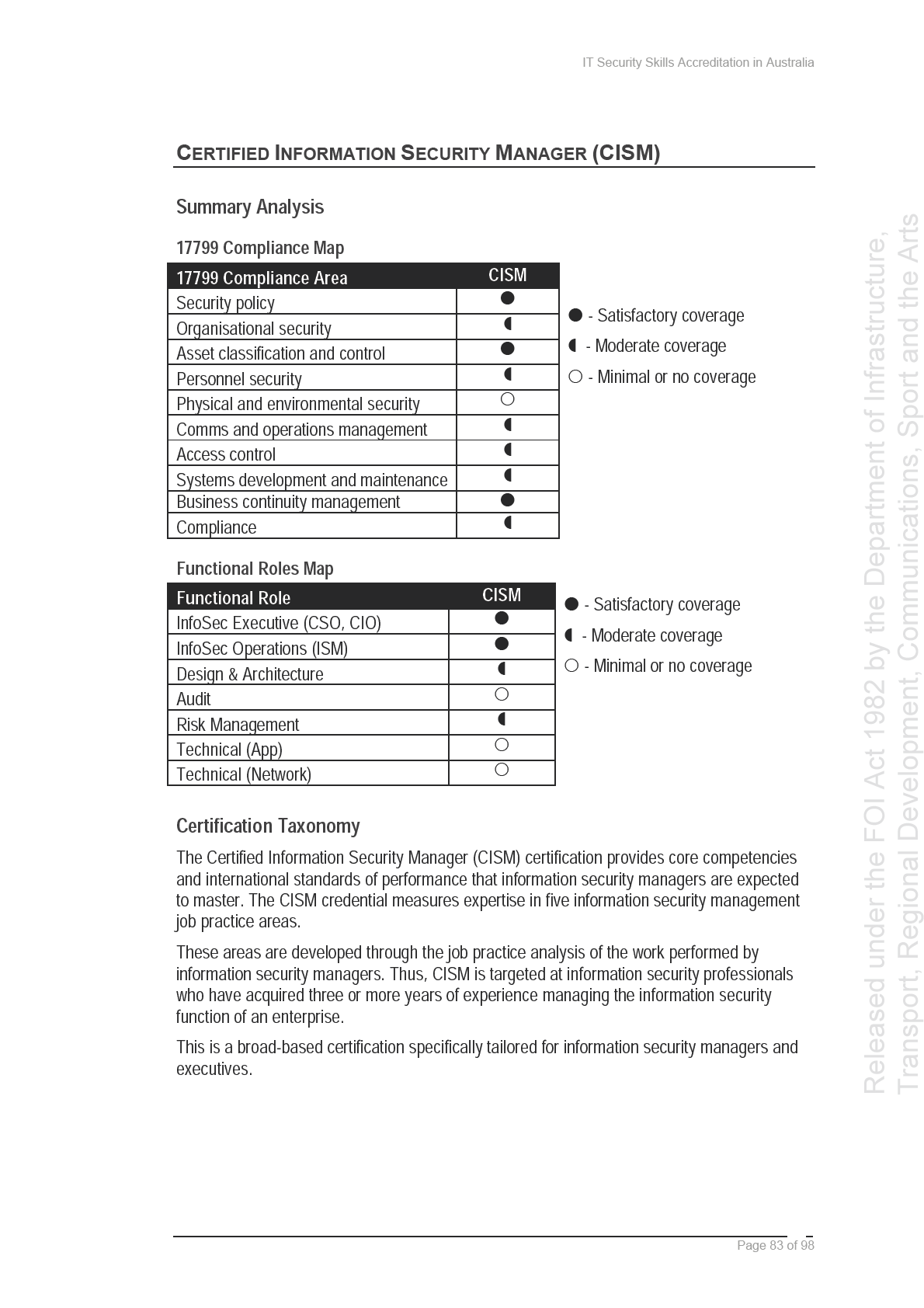
IT Security Skills Accreditation in Australia
Members of ISACA must abide by the ISACA Code of Professional Ethics. ISACA has a
formal process in place for handling complaints against certified members. The CISM
certification was accredited by ANSI to ISO Standard 17024:2003 in September 2005.
Information Security Management Job Practice Areas
Domain 1. Information Security Governance
Arts
Domain 2. Risk Management
Domain 3. Information Security Program(me) Management
the
Domain 4. Information Security Management
Domain 5. Response Management.
and
Issuer
Infrastructure,
The Information Systems Audit and Control Association (ISACA), Rolling Meadows, Illinois
of Sport
USA
Goal(s) of the Certification Body
ISACA is dedicated to serving the needs of its members, who are internal and external
auditors, CEOs, CFOs, CIOs, educators, information security and control professionals,
students, and IT consultants.
Department
Business Drivers for Implementing the Certification
the
CISM was developed out of the need for ISACA to serve an increasing number of new and
by Communications,
existing members having information security responsibilities. This includes members at all
experience levels, including information security directors, managers and consultants
responsible for IT governance, risk management and the design and management of
1982
information security within their enterprise. Many of these members had earlier earned an
information security credential such as a CISA or CISSP and were now in search of a
program that would recognise their unique managerial expertise and knowledge. In addition,
Act
ISACA identified through research and survey the increased role of the information systems
auditor in information security and a trend toward movement later in the IS auditor's career
FOI Development,
into information security management positions.
CISM's single-minded emphasis is on information security management, through the
the
management focus of its job practice areas and its management experience requirement.
CISM's requirement of information security management experience ensures that only those
who manage and oversee an enterprise's information security effort can earn it.
under Regional
Benefits of Certification to the Professional
Worldwide recognition;
Professional development opportunities as a large portion of CISMs hold
management and consulting positions;
Individuals earning the CISM certification become part of a large peer network;
Released Transport,
Certification equips the professional with the management ability to:
Page 84 of 98
IT Security Skills Accreditation in Australia
1. Align information security strategies with business objectives;
2. Identify and manage information security risks to achieve business objectives;
3. Manage an information security program;
4. Oversee and direct information security activities; and
5. Develop and manage a business continuity program.
Arts
Benefits of Certification to the Enterprise
Certification demonstrates information security management knowledge and skill;
the
Certification shows commitment to maintaining skills through future professional
development and continuing professional education;
and
Certifies that the professional has acquired professional experience and has
passed a rigorous exam;
Infrastructure,
The CISM job practice also defines a global job description for the information
of
security manager and a method to measure existing staff or compare prospective
Sport
new hires.
Target Audience
More than 1,000 CISMs serve as a chief information officer, chief executive officer
or IS security director;
More than 2,000 CISMs serve as an information security manager or in a related
Department
information security position; and
the
Nearly 1,000 CISMs are employed in security consulting or training positions.
by Communications,
Experience Requirements
Submit verified evidence of a minimum of five years of information security work experience,
with a minimum of three years of information security management work experience in three
1982
or more of the job practice analysis areas.
Act
Experience substitutions
The following security-related certifications and information systems management experience
FOI Development,
can be used to satisfy the indicated amount of information security work experience.
Two Years:
the
Certified Information Systems Auditor (CISA) in good standing
Certified Information Systems Security Professional (CISSP) in good standing
Regional
Post-graduate degree in information security or a related field (eg, business
under
administration, information systems, information assurance).
One Year:
One full year of information systems management experience
Skill-based security certifications (eg, SANS Global Information Assurance
Certification (GIAC), Microsoft Certified Systems Engineer (MCSE), CompTIA
Released Transport,
Security+).
Page 85 of 98
IT Security Skills Accreditation in Australia
The experience substitutions will not satisfy any portion of the three-year information security
management work experience requirement.
Timeliness
Due to the importance of the job task analysis and the change experienced in the information
security profession, ISACA is currently reviewing the job task analysis.
Arts
Distribution & Examination Methods
the
Preparation method - Review Seminar
and
ISACA offers review seminars prior to the scheduled exam periods. Information regarding
these seminars is available by contacting the local ISACA chapter or checking the website.
Infrastructure,
(Currently, there are no Australian seminars listed).
of Sport
Delivery of Exam
The examination is seated under supervision twice a year in December and June.
Exam Details
200 multiple-choice questions
Four hours
Department
A candidate must score a 75 or higher.
the
Identity Verification
Communications,
Verification is performed by a Testing Agency Representative.
by
Re-certification requirements
1982
In order to become and remain a CISM an individual must agree to comply with the CISM
continuing professional education program. This program requires an individual to earn a
Act
minimum of 20 hours annually and 120 hours every three years of continuing professional
education.
FOI Development,
Number of Holders
the
As at March 2005:
Over 5,000 – Worldwide
Regional
76 – Australia.
under
Cost
Early – USD$335 (ISACA members), USD$455 (ISACA non-members)
Standard – USD$385 (ISACA members), USD$505 (ISACA non-members)
Annual CPE maintenance fees of USD$40 (ISACA members), USD$60 (ISACA
Released Transport,
non-members)
Page 86 of 98
IT Security Skills Accreditation in Australia
Completeness
The CISM Domains have a moderate level of detail but do not have full coverage of ISO/IEC
17799 topics. ISO/IEC
17799 areas lacking include:
6.1 Security in Job Definition and Resourcing
7.1 Secure Areas
Arts
7.2 Equipment Security
7.3 General Controls
the
8.2 System Planning and Acceptance
8.3 Protection Against Malicious Software
and
8.5 Network Management
8.6 Media Handling and Security
Infrastructure,
9.2 User Access Management
of Sport
9.3 User Responsibilities
9.4 Network Access Control
9.5 Operating System Access Control
9.8 Mobile Computing and Teleworking
10.2 Security in Application Systems
10.4 Security of System Files.
Department
Availability
the
Registration for the CISM examination is available worldwide.
by Communications,
1982
Act
FOI Development,
the
under Regional
Released Transport,
Page 87 of 98
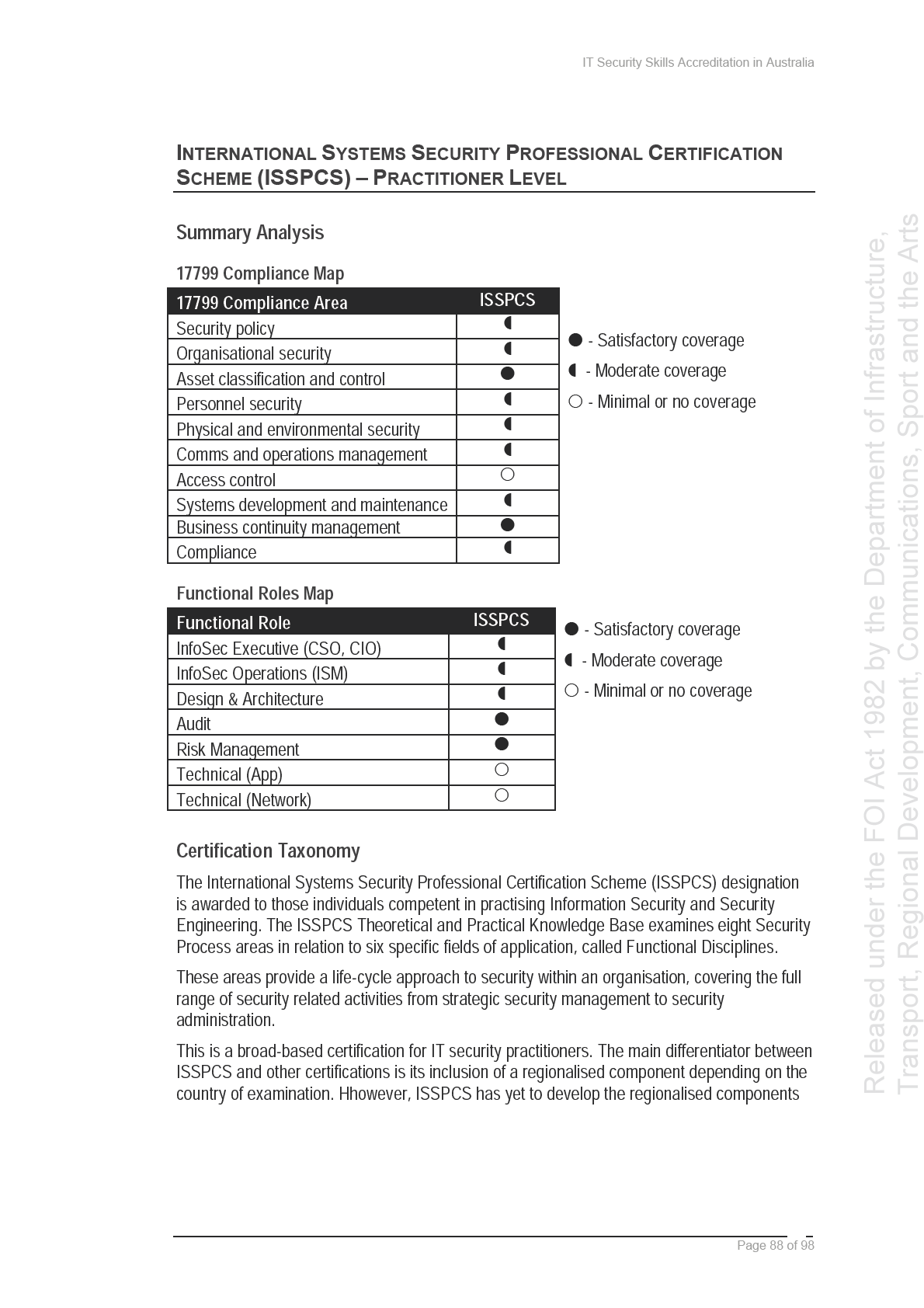
IT Security Skills Accreditation in Australia
for examination. The certification is stratified into four levels: ISSPCS Practitioner, ISSPCS
Professional, ISSPCS Mentor and ISSPCS Fellow.
Members of ISSPCS are bound by the ISSPCS Code of Ethics. ISSPCS is currently awaiting
approval from the Academic Board and ISSEA on the proposed complaints process against
ISSPCS members.
Arts
ISSPCS Security Process Areas
Strategic Security Management
the
Compliance (Standards / Legal)
Asset Identification, Classification and Valuation
and
Security Risk Analysis and Assessment
Infrastructure,
Security Risk Treatment (Management of the Risk)
Operational Security Management
of Sport
Security Operations: Normal Conditions
Security Operations: Abnormal Conditions.
Issuer
The International Systems Security Engineering Association, Herndon, Virginia, USA
Department
Goal(s) of the Certification Body
the
The ISSPCS developers and ISSEA have striven to develop and implement a professional IT
and Systems Security Certification Scheme that has wide credibility and jurisdiction and is
by Communications,
genuinely international.
Business Drivers for Implementing the Certification
1982
Presently, organisations are implementing a multitude of enterprise-wide security solutions
encompassing people, technology and physical domains in order to deal with the availability,
Act
authenticity, integrity, confidentiality and non-repudiation of services. One of the major
challenges for the modern organisation is the ability to recognise talent, skills and experience
FOI Development,
when it comes to the development and implementation of a security regime capable of
protecting the organisation’s assets. For the security professional, the problem is the lack of
the
certifications available which focus on the general principles of security and their essential
foundations.
To address these issues, the ISSEA oversaw the implementation of a global and open
Regional
certification scheme for security professionals that addresses the shortfalls of traditional IT
under
security certifications by founding the scheme on essential principles of security. The ISSPCS
development team is involved in the continual development of the certification program.
Benefits of Certification to the Professional
Wide credibility, jurisdiction and international;
Released Transport,
The certification is constantly updated throughout the year;
Vendor-neutral;
Page 89 of 98
IT Security Skills Accreditation in Australia
Provides cost-effective certification focusing on the general principles of security
and the essential foundations;
Provides a theoretical and practical base on which to build fundamental skills;
Addresses the shortfalls of traditional IT security certifications by founding the
scheme on essential principles of security;
Open scheme which is open to all IT and systems security professionals; and
Arts
Various levels of certification may be achieved by successful completion of
certified examinations and/or interviews.
the
Benefits of Certification to the Enterprise
Ability to recognise talent, skills and experience;
and
Credible, comprehensive, cost-effective, international in scope;
Infrastructure,
Various levels of the certification offer an indication of professional experience and
knowledge;
of Sport
Independent scheme with no commercial bias to any vendor or group of vendors;
The scheme requires the professional to have evidence of continuing
development;
Certification does not simply rely on the regurgitation of a body of knowledge, but
is instead founded on demonstrating an ability to apply process and methodology,
as well as an understanding of security knowledge and techniques; and
Department
Scheme is not exclusively IT but also reflects the systems approach, including
physical personnel and technological.
the Communications,
Target Audience
by
The ISSPCS is a four-level program is aimed at developing IT and systems security
professionals. The Practitioner examination is the entry level for all applicants.
1982
The ISSPCS program is only conducted in English. Exams are held in Australia, Canada and
the US.
Act
Experience Requirements
FOI Development,
ISSPCS candidates must have an IT or related degree, and three years of information
security experience. The Practitioner certification is valid for three years.
the
Grandfathering Scheme
Suitably qualified professionals may apply for an ISSPCS Practitioner certification without
under Regional
having to sit or pay for the examination, by utilising the ISSPCS Grandfathering Program. To
gain an ISSPCS Practitioner via the Grandfathering Program, the applicant must meet or
exceed these requirements:
Applicant must hold at least one of the following certifications; a current CISSP,
CISM, GIAC Security Expert Certification, or SSE-CMM Appraiser Certification;
Released Transport,
Applicant must be able to demonstrate no less than five years of work experience
in the information security field;
Page 90 of 98
IT Security Skills Accreditation in Australia
Applicant must provide current resume, showing work history that is relevant to
the information security or information security engineering fields, and summaries
of engagements in information security activities;
Applicant must provide one personal character reference, written by an associate;
Applicant must provide one professional reference written by an associate
describing their work exposure, work quality and work ethic; and
Arts
Applicant must have successfully completed an ISSPCS Grandfathering Scheme
Application, including agreement to uphold the ISSPCS Code of Ethics.
the
Timeliness
and
The ISSPCS development team is involved in the continual development of a certification
programme that is credible, comprehensive, cost-effective, international in scope, and
Infrastructure,
genuinely open.
of Sport
Distribution & Examination Methods
Preparation method – Reference Resources
Each ISSPCS level has specific resources that are freely downloadable. There are currently
six Practitioner reference resources available.
Department
Delivery of Exam
The examination is seated under supervision, every three to six months.
the Communications,
Exam Details
by
Closed book
Four hours
1982
A candidate must score 60 per cent or higher
Identity Verification
Act
Candidates must bring current and valid photo identification to the examination venue.
FOI Development,
Re-certification requirements
the
ISSPCS members must achieve a defined number of Activity Points (APs) over the three-year
term of their certification. For an ISSPCS Practitioner, 750 APs are required. When the
applicant re-certifies, they must have equalled or exceeded the required number of APs for
their certification.
under Regional
Number of Holders
As at March 2005:
34 approved from grandfathering, 200 applicants awaiting approval.
Released Transport,
Page 91 of 98
IT Security Skills Accreditation in Australia
Cost
Standard – AUD$500 / CAD$500 / USD$400
Triennial recertification fee of AUD$300.
Completeness
The Theoretical and Practical Knowledge Base has an adequate level of detail but does not
Arts
have full coverage of ISO/IEC
17799 topics. ISO/IEC
17799 areas lacking include:
the
6.3 Responding to Security Incidents and Malfunctions
7.1 Secure Areas
and
8.6 Media Handling and Security
9.2 User Access Management
Infrastructure,
9.3 User Responsibilities
of Sport
9.4 Network Access Control
9.5 Operating System Access Control
9.8 Mobile Computing and Teleworking.
Availability
The ISSPCS examination program is currently only available to Australia, Canada and the
Department
US.
the
by Communications,
1982
Act
FOI Development,
the
under Regional
Released Transport,
Page 92 of 98
IT Security Skills Accreditation in Australia
[ISIG 2005]
Professional Membership Requirements; ISIG; 2005
http://www.isig.org.au/Professional%20Membership.htm
[ISSPCS 2005]
About the ISSPCS Practitioner Certification; ISSPCS; 2005, ISSPCS official
website
http://www.isspcs.org/cert/practitioner.php
[ITPC 2005]
Infosec Training Paths and Competencies; ITPC; 2005, ITPC official website
http://www.cabinetoffice.gov.uk/infosec/index.asp
[Jenkins 2005]
Industry accreditation moves closer; Jenkins, C; 15 March 2005, The Australian IT
http://australianit.news.com.au/articles/0,7204,12550458%5E15334%5E
Sport and the Arts
%5Enbv%5E15306-15317,00.html
[LeMay 2005a]
Mixed views on AU IT security accreditation; LeMay, R; 15 March 2005,
ZDNet
Australia
http://www.zdnet.com.au/news/security/0,2000061744,39184626,00.htm
[LeMay 2005b]
Security group enters accreditation race;
LeMay, R; 5 April 2005, ZDNet Australia
http://www.zdnet.com.au/news/security/0,2000061744,39187091,00.htm
[Mandla 2005]
Certification standards; Mandla, E; 10 February 2005, ZDNet Australia
Communications,
http://www.zdnet.com.au/news/security/0,2000061744,39180456,00.htm
[Mullins 2005]
Security certification: What to look out for?; Mullins, M; 11 March 2005, CNET Asia
http://asia.cnet.com/enterprise/manage/0,39035818,39221122,00.htm
[Parker 2005]
What value your security certification?;
Parker, D; 29 March 2005, The Register
Act 1982 by the Department of Infrastructure,
http://www.theregister.co.uk/2005/03/29/security certification/
Development,
[PITAC 2005]
Report to the President – Cyber Security: A Crisis of Prioritization; President’s
Information Technology Advisory Committee; February 2005, PITAC
http://www.nitrd.gov/pitac/reports/20050301 cybersecurity/cybersecurity.pdf
[UKAS 2005]
Certification Body Schedules; United Kingdom Accreditation Services; 2005
under the FOI
http://www.ukas.com/about accreditation/accredited bodies/certification
body schedules.asp
2004
Released Transport, Regional
Page 94 of 98
IT Security Skills Accreditation in Australia
[ANSI 2004a]
Accredited Personnel Certification Programs; American National Standards
Institute; June 2004
http://public.ansi.org/ansionline/Documents/Conformity%20Assessment/Personnel
%20Certifier%20Accreditation/ISO-
IEC%2017024%20General%20requirements%20for%20bodies%20operating%20c
ertification%20of%20persons/Client%20Companies%20and%20Applicants/Directo
ry%20of%20Accredited%20Programs-17024.pdf
[ANSI 2004b]
Accredited Personnel Certification Programs-Applicants; American National
Standards Institute; December 2004
http://public.ansi.org/ansionline/Documents/Conformity%20Assessment/Personnel
%20Certifier%20Accreditation/ISO-
IEC%2017024%20General%20requirements%20for%20bodies%20operating%20c
ertification%20of%20persons/Client%20Companies%20and%20Applicants/Directo
Sport and the Arts
ry%20of%20Applicants-17024.htm
[APEC 2004]
IT Skills Report – APEC; APEC; 2004, APEC Telecommunications and Information
Working Group
http://www.apectel29.gov.hk/download/estg 05.doc
[Fundaburk
The Education of Information Security Professionals: An Analysis of Industry
2004]
Needs vs. Academic Curriculum in the 21st Century; Fundaburk, A; 2004,
Bloomburg University
http://cob.bloomu.edu/afundaburk/personal/The%20Education%20of%20I
Communications,
nformation%20Security%20Professionals.ppt
[ISIG 2004]
Professional Recognition Update; ISIG; 20 October 2004,
ISIG Website
http://www.isig.org.au/Professional%20Recognition%20Update.htm
[ISPWG 2004]
The Institute for Information Security Professionals – A Blueprint; Information
Act 1982 by the Department of Infrastructure,
Security Professionals Working Group; 7 December 2004,
Information Security
Professionals Working Group
Development,
[HKCS 2004]
Commonly Accepted Audit or Assessment Mechanism to Certify Information
Security Standards – HKCS Response; HKCS; 6 October 2004
http://www.hkcs.org.hk/doc journal/securitybureau.pdf
[Norris 2004]
IT Security Workforce Development and the Role of Professional Certification;
under the FOI
Norris, J. S; March 2004, Federal Information Systems Security Educators
Association
[SA 2004]
AS ISO/IEC 17024-2004: Conformity Assessment - General requirements for
bodies operating certification of bodies; Standards Australia; 2004
Released Transport, Regional
Page 95 of 98
IT Security Skills Accreditation in Australia
[Varadharajan
ICT Security and Certification;
Varadharajan, V; 14 December 2004, Information
2004]
Age
http://www.infoage.idg.com.au/index.php/id;319104870;fp;16;fpid;0
2003
[Ames, Gaskell
Registration and Certification of Information Security Professionals; Ames, M;
& Muir 2003]
Gaskell, G; Muir, M;
ISIG Website
http://www.isig.org.au/AusCERT/ISIG%20Discussion%20Paper.htm
[Bogue 2003]
What makes a certification valuable?; Bogue, R L; 16 June 2003, ZDNet Australia
http://www.zdnet.com.au/jobs/resources/0,2000056675,20275390,00.htm
[Gray 2003]
CISSP security certification under fire from academics;
Gray, P;14 May 2003,
Sport and the Arts
ZDNet Australia
http://www.zdnet.com.au/news/security/0,2000061744,20274484,00.htm
[EURIM 2003]
EURIM – IPPR E-Crime Study; Partnership Policing for the Information Society,
Working Paper 5: Growing the Necessary Skills; EURIM; 10 November 2003,
EURIM
2002
[IFIP 2002]
TC-11 Statement on Information Security Professionals (Decided during annual
meeting on 5 May 2002 in Cairo, Egypt)
Communications,
[Jarmin 2002]
ICTSO certification Scheme; Jarmin, M; 1 October 2002, MAMPU
http://www.ktkm.gov.my/images/ictso.ppt
[Sundt 2002]
Information Security Consultancy – A Study for The Department of Trade and
Industry; Sundt, C; May 2002
Act 1982 by the Department of Infrastructure,
http://www.dti.gov.uk/industry files/pdf/psirep.pdf
Development,
2001
[SA 2001]
AS NZS ISO IEC 17799-2001 Information Technology – Code of practice for
information security management; Standards Australia; 2001
[Wilson 2001]
IN TRAINING: Security courses look for students to fill places; Wilson, E; 18
September 2001,
The Age
under the FOI
http://www2.ma.rmit.edu.au/Kepler/academicstaff/Asha/agearticle.html
1994
Released Transport, Regional
Page 96 of 98
IT Security Skills Accreditation in Australia
[NSTISSI 1994]
NSTISSI No. 4011 – National Training Standard for Information Security
(INFOSEC) Professionals; NSTISS; 1994
http://security.isu.edu/pdf/4011.pdf
Arts
the
and
Infrastructure,
of Sport
Department
the
by Communications,
1982
Act
FOI Development,
the
under Regional
Released Transport,
Page 97 of 98


 SIFT – Our Profile
SIFT – Our Profile
Founded in 2000, SIFT is a leading Australian pure-play information security
consulting, intelligence and training firm. We specialise in the delivery of
independent advice, reviews and recommendations to the senior
management of large, highly regulated organisations.
Our focussed provision of information security advice and assurance
Arts
services within the context of industry and country-specific regulatory
requirements is unique. Our commitment to our clients is the ongoing
the
delivery of concrete, specific and measured steps across the broad
spectrum of information security body of knowledge.
and
SIFT has built long-term relationships with major clients and information
security stakeholders in both the public and private sectors, providing
Infrastructure,
exceptional customer focus throughout our business units. Through our
of
security intelligence and industry and regulatory relationships, we are
Sport
uniquely positioned to advise on information security within the Australian
context.
Also realising the importance of information security in the wider community,
SIFT is a sponsor of the Internet Industry Association (IIA) SME security
portal, and provides pro-bono consulting services and financial support to
The Inspire Foundation & Reachout! – a service that uses the internet to
Department
provide much-needed information, assistance and referrals to young people
going through tough times.
the
Our Services
by Communications,
Leveraging our unique perspective of information security issues in the
Australian context, SIFT offers its clients a range of services:
Consulting
1982
Penetration Testing & Risk Assessment
Information Security Governance, Compliance & Reporting
Act
Security Reviews, Au
n
dits a d Benchmarking
Privacy Strategy & Audit.
FOI Development,
Intelligence
Policy & Procedure Development & Review
the
Information Availability & Aggregation Reviews
Product & Vendor Reviews/Recommendations
ust
C om Research Reports.
under Regional
Training
Introduction to Encryption & PKI
Information Security: Tactical Information Control
Part of the proceeds from this
Industry-Based Training
project will be used to support
the work of the Inspire
Custom Training Programs.
Foundation &
Reach Out!
Released Transport,





















