Obligations to sources
MEAA Journalist Code of Ethics
ABC Editorial Policies
3) Aim to attribute information to its source.
5.7 Assurances given in relation to conditions of
Where a source seeks anonymity, do not agree
participation, use of content,
confidentiality or
without first considering the source’s motives
anonymity must be honoured except in rare
and any alternative attributable source.
Where
cases where justified in the public interest.
confidences are accepted, respect them in all
circumstances.
4
Pages 5-19 redacted: section 42: legal professional privilege
RISK EVALUATION QUESTIONS TO ASK
Who is the source?
Low/Medium: Private individuals, small to
How have they found you? On what platform are they
medium enterprise, local governments Medium
communicating with you?
Large companies, state governments, wealthy
Are they reliable? Are they say who they are?
individuals
What are the risks for the source and you?
High: Non-national security-related federal
agencies, federal police, government agencies,
What is their tech literacy?
state police
What kind of information might they have access to?
Very: High National security agencies, foreign
What legislation might it be covered by?
security agencies
20

Signal
● Open source code (peer reviewable), similar to OTR encryption
● Has a VOIP calling service
● Linked to phone numbers (automatically populates contacts)
● No key ID
● Autodestruct function
Threema
● Not open source (audited in August 2015 by CN Lab)
● Messaging service only
● Has a Key ID (helpful for placing on Twitter accounts, email signatures)
● VOIP calling service
Wickr
●
Wickr
● Not open source (audited in August by Aspect Security)
● Linked to phone numbers and emails
● Self destructing messages
● Key ID
22
HOW TO GET DOCUMENTS SECURELY
Questions to think about.
Think about transmission: Use hard copies where
possible or encrypted means
1. How many others can access this info?
2. Is this access logged?
Think about metadata and document properties:
3. Have they already done this in a manner
Could information in the documents reveal your
that might expose them?
source if published?
4. How are they planning to share them
with you?
Think about how you reveal what you have
5. Is this the safest method?
possession of: Consult with legal about language
around documents
23





First contact
Contacting a potential source or whistleblower for the first time is a vital moment. If not done
securely it can, later, allow others to backtrack and establish who your source was.
There are numerous ways to contact a source that limits the risk of later compromising them –
none are perfect and you will have to consider different methods for each source. Some options
to consider:
➢
In-person contact.
➢ Call or message from
a phone or device not connected to you
➢ Use an
encrypted app such as Signal to message or call them.
➢
Encrypted online communications using tools such as Tor and/or Tails.
Once you have made contact,
you are then responsible for ensuring neither you nor the source
do anything that may compromise the promise of confidentiality you have given.
Document receipt, handling and publication
Another area where journalists fail their sources is the manner in which they receive, handle and
publish sensitive documents.
When receiving documents ask these questions, at a minimum:
➢ Did the source send them to you from
a device associated with them?
➢ Are they
copies (i.e., photos) or originals?
➢ Are they print-outs, and if so
do they retain information that can identify the printer?
➢ Are they on a USB, and if so does the USB or the files
retain a digital fingerprint?
Passwords
Passwords can often be strengthened using a few basic steps.
➢ Strong passwords. There are many ways to create secure passwords. For an explainer
check out this two minute video1 by the Electronic Frontier Foundation, or this video2
from the Checkout. This well-known comic3 explains some common myths about secure
passwords.
➢ Two-factor authentication (also known as 2FA). That means a login process that requires
a second factor of authentication after you enter your password. (Preferably not text.)
Mobile phones
1 https://ssd.eff.org/en/module/animated-overview-how-make-super-secure-password-using-dice
2 https://www.facebook.com/checkouttv/videos/1680569738648977/
3 https://imgs.xkcd.com/comics/password strength.png
30
Mobile phones are one of the things most likely to cause you and/or your source to be
compromised. Good habits when using your phone, and educating your source on those same
habits, are one of the best things you can do to protect them.
For messaging and voice calls
always use Signal4. To make it more secure read these tips.5
Another option is to use a phone not connected to you – but remember that repeated use of
such a phone may create a pattern that can identify your source.
Email
For sensitive communications
always use encrypted email services
such as ProtonMail,6
which is a free, easy to use option – but only for low-level threats. For high-level threats refer to
the “Other tools” section below.
Here are some things to think about if a source wishes to communicate with you via email:
➢ Don’t use ProtonMail on internet connections associated with them (i.e., their home wifi
or their work computer).
➢ Encrypted email services such as ProtonMail are most secure when both the sender and
the recipient are using the service.
➢ Don’t use gmail or similar unencrypted webmail services.
Post
Physical mail is insecure. Packages sent from a source to you via the post can easily be
intercepted enroute or by any of the dozens of people who come and go from our mailrooms
every day.
Other tools
One of the most secure ways you can communicate with, and receive information from,
sensitive sources involves using a computer operating system called Tails.7 Combined with the
use of the anonymising software Tor8 and some good digital hygiene, it provides best practice
protection for you and your sources.
However, Tails and Tor require some practice. If you’re interested in learning more let us know.
And if you want to do some reading on your own about information security for journalists, you
could do worse than starting here.9
Thanks!
4 https://signal.org/
5 https://pastebin.com/raw/YFFxRQvH
6 https://protonmail.com/
7 https://tails.boum.org/
8 https://www.torproject.org/
9 https://tcij.org/sites/default/files/u11/InfoSec%20for%20Journalists%20V1.3.pdf
31
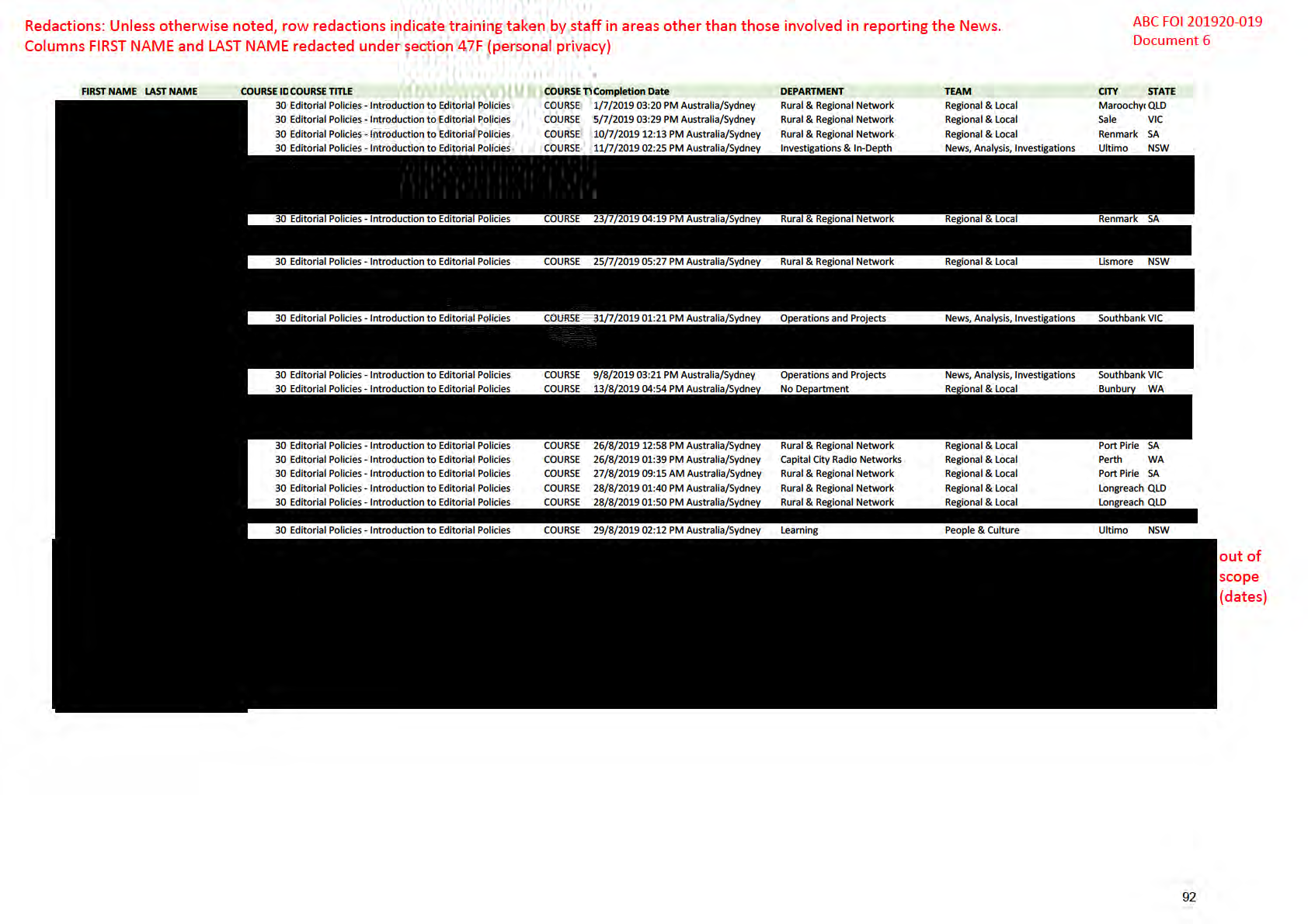
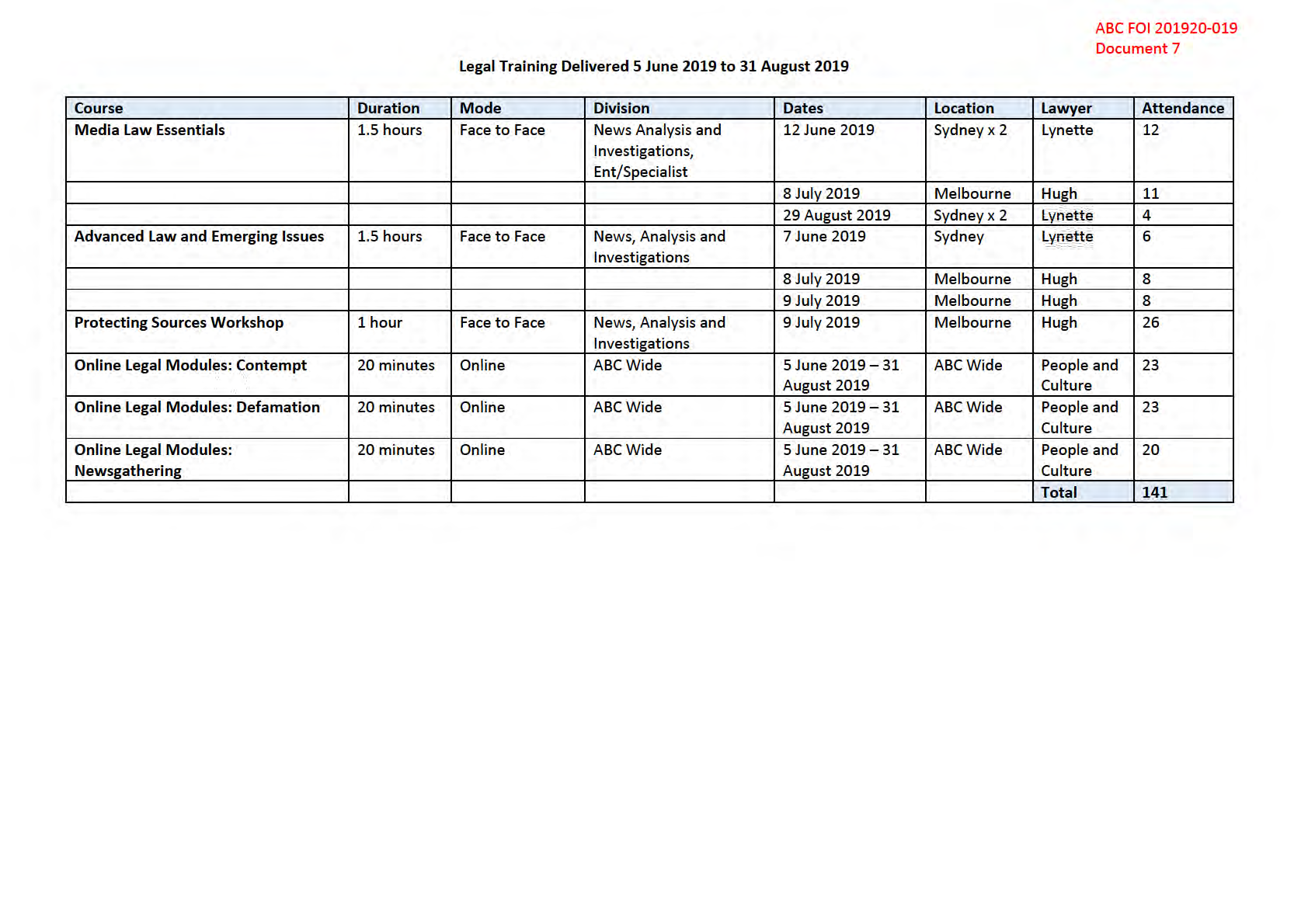
Redactions: Unless otherwise noted, row redactions indicate training taken by staff in areas other than those involved in
ABC FOI 201920-019
reporting the News. 'Name' column redacted under section 47F (personal privacy)
Document 4
EDITORIAL POLICY TRAINING FOR THE CALENDAR YEAR 2019
Name
Division
Date Trainer
Venue
Nature of training
Duration
out of
scope
(dates)
32
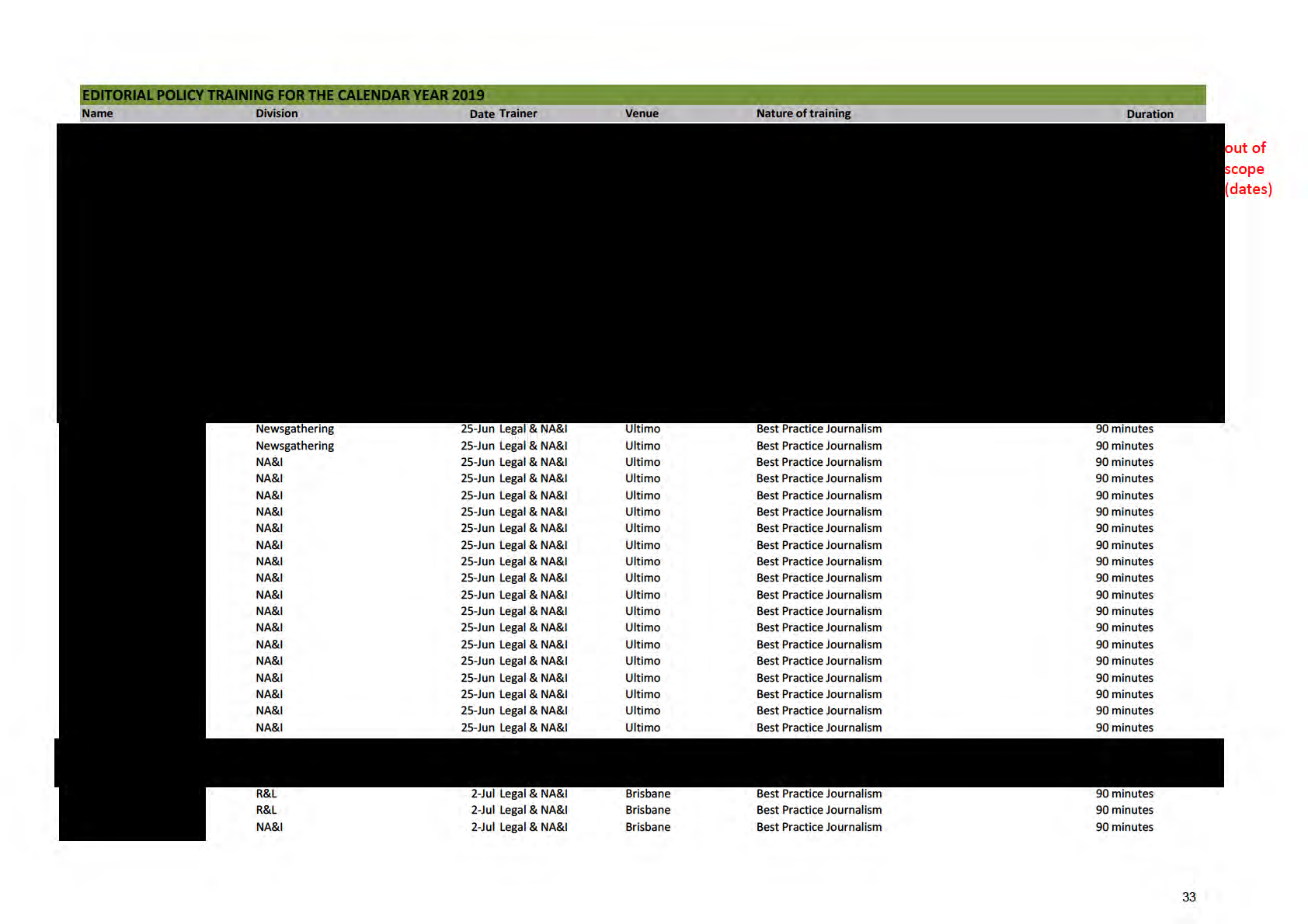

EDITORIAL POLICY TRAINING FOR THE CALENDAR YEAR 2019
Name
Division
Date Trainer
Venue
Nature of training
Duration
NA&I
4‐Jul Legal & NA&I
Ultimo
Best Practice Journalism
90 minutes
NA&I
4‐Jul Legal & NA&I
Ultimo
Best Practice Journalism
90 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
NA&I
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
R&L
25‐Jul Jane Connors
Brisbane
Refresh for digital/social producers
75 minutes
36
EDITORIAL POLICY TRAINING FOR THE CALENDAR YEAR 2019
Name
Division
Date Trainer
Venue
Nature of training
Duration
NAI
27‐Aug Mark Maley
Sydney
Induction & Sources
60 minutes
out of
scope
(dates)
37
Pages 39-91 redacted: out of scope of request (timeframe)